Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
CISOs: Cyber Criminals Don’t Want You to Know This One Weird Trick to Alleviate Insider Threat Nightmares
By Liberty Williams · September 25, 2023
Every now and then, nearly every CISO wakes up at 2 am, sweating and/or swearing, from a nightmare involving News Headlines, Insiders, Data Breaches, Lawyers, Lawsuits, and Liability! We know because You tell us you do. We know because you call Trellix Incident Response when the nightmare slips into reality. We know because we had the same nightmares. Trellix is here, with you and for you, and we can do something about it!
Why does it matter:
Many organizations have landed in the news via alleged data breaches. The US Federal Health and Human Services Office of Civil Rights (HHS OCR) regularly publishes enforcement highlights including many involving inappropriate insider access. The US Federal Trade Commission (FTC), US HHS OCR, The US Securities and Exchange Commission (SEC), the European Data Protection Supervisor (EDPS), and European Data Protection Board (EDPB) require breach notifications. Thanks to these notification requirements, and the work of law enforcement attorneys, industry researchers, and journalists, CISOs in 2023 have a growing understanding of just how pervasive these threats are.
Verizon’s 2023 Data Breach Investigations Report asserts that 19% of data breaches are perpetrated by inside actors, and that 89% of these actors are motivated by financial reasons, and 13% are motivated by grudges. In 2022, a former Amazon administrator was convicted of stealing customer data by abusing privileges. The US Department of Justice Alleged in 2022 that a former Atlanta, GA area hospital employee stole PII from the hospital’s database as part of an alleged conspiracy to defraud $30 million in Covid benefits. In 2021, the US Department of Justice obtained a conviction in the case of a foreign government employee who attempted to bribe a Boeing engineer to disclose industrial trade secrets pertaining to composite fan blades. In 2020, Primera Blue Cross agreed to pay $6.85 million to HHS OCR to settle potential violations of the Health Insurance Portability and Accountability Act.
Understand the problem:
The US Cybersecurity and Infrastructure Security Agency (CISA) defines several types of Insider Threats. In this blog we’ll focus on intentional insider threats, also called malicious Insiders. Intentional insider threats do not follow the classic Advanced Persistent Threat cyber kill-chain, which might look something like this:
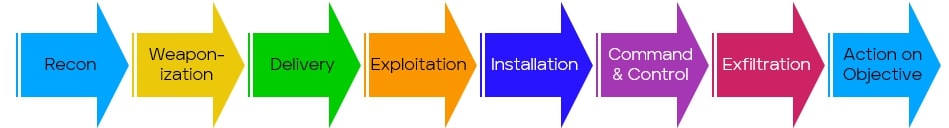
Insider threats do not need to weaponize, deliver, install or command & control. Insiders already have access, sometimes much more than they needed to get the (dirty) job done. The insider threat kill-chain looks more like this:

When examining each step and how they work together to exfiltrate data, please note that this isn’t like the mathematics acronym, Please Excuse My Dear Aunt Sally. These steps can happen out of order or even contemporaneously, and some steps may be skipped by less experienced malicious insiders (to your benefit). If one is familiar with MITRE Corporation’s Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK) knowledge base and ATT&CK Navigator, you’ll notice a lot of similarity!
- Recon, short for Recon-naissance: A French origin loan-word that means looking around, seeing stuff, gathering intel, learning the lay of the land, finding out where our goodies are kept and where our security is weak and/or trusting.
- Our recon stage is analogous to the ATT&CK verticals Reconnaissance and Discovery
- Escalation/Evasion: This step is all about making an end run around existing security controls. Our malicious insider “escalates” their privileges, gaining access they shouldn’t have, and “evades” security controls, monitoring tools, logging, and the watchful eyes of their chain of command. Wish our rainforests could learn to evade logging.
- These are the same as the ATT&CK verticals for Privilege Escalation and Defense Evasion
- Collection: Whether automated or manual, this step is about gathering all the juicy data and intellectual property our malicious insider found at the Recon step. Smarter insiders will keep the data in separate locations, but it’s not uncommon to find 20k credit card numbers or email addresses in a text file on your insider’s laptop.
- This is the same as the ATT&CK vertical of the same name
- Encryption/Obfuscation: During this step, our malicious insider will attempt to confuse us as to the nature of the data they are transmitting. This can take many forms, from the abuse of TLS, embedded archives and files within files, crazy techniques like DNS leaking, Steganography or Z29vZCBvbGQgZmFzaGlvbmVkIEJhc2U2NCBFbmNvZGluZy4
- ATT&CK: T1132 Data Encoding, T1001 Data Obfuscation, T1573 Encrypted Channel, etc…
- Exfiltration: This is what our malicious insider has been working for, the chance to get paid by delivering YOUR intellectual property, YOUR customer’s private data, YOUR classified data!
- This maps to the ATT&CK vertical Exfiltration, and if you’re dealing with a Grudge motivation, (TA0040).
Disrupting this insider threat kill chain therefore seems like a daunting task. How do I stop folks from looking around for stuff they can steal without stopping them from doing the jobs I’m paying them for? How do I place technology controls in the way of my Domain Administrators and Network Administrators without breaking my network and my apps? How do I leverage the cost, flexibility, and ecological benefits of cloud computing without risking it all on one angry AWS admin?
Define the solution:
We can borrow some expertise from our friends at the US National Institute of Standards and Technology (NIST), who helpfully publish their 800 series Special Publications just for cybersecurity. These requirements largely focus on the strict requirements of the US Government’s civilian agencies (and Japanese defense contractors), but they are broadly applicable to any organization or institution that has information that could be considered sensitive (aka everyone on earth). The European Union Agency for Cybersecurity (ENISA) is, as of 9/25/2023, still working on their certification framework. International Organization for Standardization and International Electrotechnical Commission (ISO/IEC) 27002 and 27017, and the Center for Information Security (CIS) Critical Controls largely cover the same ground.
Key publications:
- NIST SP 800-207 Zero Trust Architecture
- NIST SP 800-53 Rev 5 Security and Privacy Controls for Information Systems
- Check the end of the post for further reading!
I realize that’s a whole lot to handle, and you signed up to read just a single blog post, so let’s just focus on a few concepts and controls from Zero Trust and NIST SP 800-53. We’ll pick a few that are particularly relevant to the insider threat kill-chain. Once we’ve got those laid out, we can easily map the controls NIST contemplates to capabilities and configuration options within the Trellix product portfolio. We’ll reference CSF.Tools for further details on these controls
An Extremely Non-Exhaustive list of relevant controls:
- AC-3: Access Enforcement - CSF Tools
- AC-3(3): Mandatory Access Control - CSF Tools
- AC-3(7): Role-based Access Control - CSF Tools
- AC-3(8): Revocation of Access Authorizations - CSF Tools
- AC-3(10): Audited Override of Access Control Mechanisms - CSF Tools
- AC-3(11): Restrict Access to Specific Information Types - CSF Tools
- AC-3(13): Attribute-based Access Control - CSF Tools
- AC-4: Information Flow Enforcement - CSF Tools
- AC-4(1): Object Security and Privacy Attributes - CSF Tools
- AC-4(3): Dynamic Information Flow Control - CSF Tools
- AC-4(4): Flow Control of Encrypted Information - CSF Tools
- AC-4(5): Embedded Data Types - CSF Tools
- AC-4(6): Metadata - CSF Tools
- AC-4(8): Security and Privacy Policy Filters - CSF Tools
- AC-4(9): Human Reviews - CSF Tools
- AC-5: Separation of Duties - CSF Tools
- AC-21(1): Automated Decision Support - CSF Tools
- AU-6: Audit Record Review, Analysis, and Reporting - CSF Tools
- MP-2: Media Access - CSF Tools
- MP-3: Media Marking - CSF Tools
- IA-7: Cryptographic Module Authentication - CSF Tools
- SC-12: Cryptographic Key Establishment and Management - CSF Tools
- SC-13: Cryptographic Protection - CSF Tools
- Zero Trust
- Access to individual enterprise resources is granted on a per-session basis.
- Access to resources is determined by dynamic policy—including the observable state of client identity, application/service, and the requesting asset—and may include other behavioral and environmental attributes.
Now that we have a condensed list, the next step is to map things to our insider threat kill-chain:
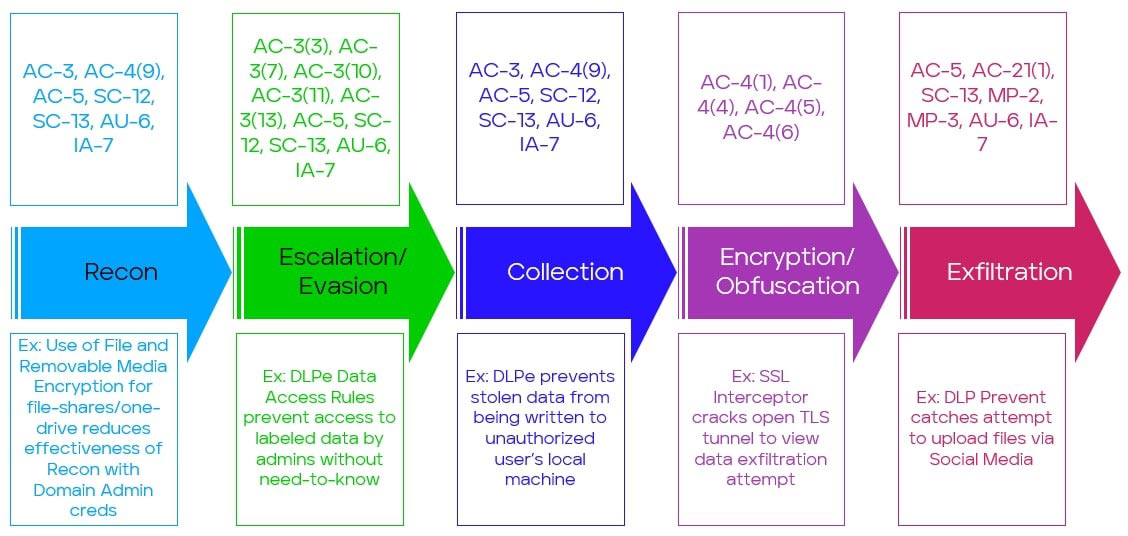
Note that many of the techniques that help us frustrate our malicious insider during Recon also help us to frustrate them during collection.
Putting theory into practice:
While we can’t cover every single way Trellix helps protect against insider threats in a single blog post, we can at least provide some key examples.
Trellix XDR (extended detection and response), has analytics capabilities powered by Machine Learning that can detect unusual usage and unusual logins. This can help identify potential credential theft and reconnaissance activities, especially when performed with pre-designated privileged user accounts subject to higher levels of scrutiny.
Local Privilege Escalation attempts can be disrupted using Endpoint Security (ENS) through Access Protection Rules and Exploit Prevention Rules. There are many generic rules available, but both countermeasures give us the ability to create customized detection/blocks for new and unique privilege escalations. In this example, Trellix Insights provided IOCs and countermeasure recommendations for PwnKit: Trellix Insights: PwnKit, a local privilege escalation exploit for Unix and Linux Systems (CVE-2021-4034). ENS comes with self-protection features to make it very difficult to evade when properly configured.
Remote (network based) Privilege Escalation attempts can be disrupted using Trellix Intrusion Prevention System (IPS, formerly NSP) and Trellix Network Security Appliance (NX). While not every privilege escalation will take place over HTTP/HTTPS, a quick Ctrl-F of KB50726 shows 78 signatures aimed at disrupting specific application privilege escalations. These signatures can be customized as well, based on IOCs provided by your favorite threat feed (I know it’s Trellix Insights, mine too!).
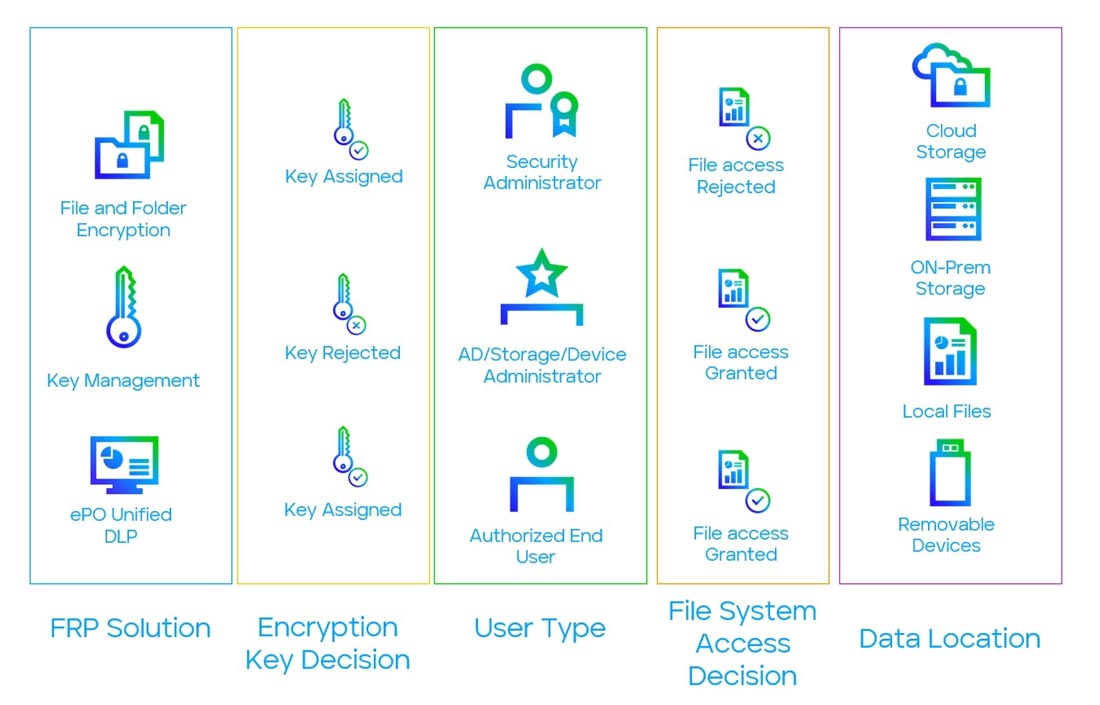
Separation of Duties can dramatically reduce the value and increase the complexity of Privilege Escalation (and Credential Theft) while also disrupting Recon and Collection. We can use Trellix File and Removable Media Protection (FRP) file level encryption to effectively enforce Separation of Duties in our File Storage services. In a traditional AD managed environment, file permissions are maintained by Domain Administrators, and even when they are explicitly denied access to a folder it is possible for them to recover access. There is often no way around granting at least someone this access. After all, how else could they run a backup or perform deduplication efforts?
By adding a second layer to our file access process, we can effectively add Policy Based Access Controls wherever our sensitive data is kept. When properly configured, FRP loads encryption keys only when an encrypted resource is requested, and only when the currently logged-in user has been appropriately assigned the relevant key. These keys are ideally managed by a separate group from File Permissions. This remediates the situation where any single administrator can simply grant themselves access to sensitive data. FRP comes with self-protection features to make evading this encryption difficult.
Now that we’ve explored ways to disrupt Recon, Escalation/Evasion, and Collection, it’s time to take a whack at Encryption/Obfuscation and Exfiltration. We can look to Trellix Data Loss Prevention (DLP) and Trellix Network Security (NX), Packet Capture (PX), and Investigation Analysis (IA) network components, as well as the host-based Data Loss Prevention Endpoint (DLPe), and Trellix H-Endpoint X-Security (HX).
Specifically with a view to insider threats, DLPe provides us with the following capabilities (but has many others):
- Data Labels – DLPe can apply Trellix Data Labels (Called Classifications or Fingerprints) and Azure Information Protection (AIP) Labels, either automatically based on automated rules or manually by user action.
- Persistent Labels – DLPe can apply labels based on copy/pastes, screenshots, and transformations (compression/encryption) applied to already labeled data.
- Discovery – DLPe can search for and label, encrypt, and quarantine data stored locally.
- Policy Based Access Control/Automated Decision Support – DLPe is able to allow or prevent access to and transmission of data based on organization defined access control policy.
- Human Review – DLPe allows legitimate end users to reach out to designated agents for temporary bypass of automated decision enforcement.
- Auditing – DLPe produces auditable events that can offer insight into naïve/early data exfiltration attempts, and offer a record for retrospective review.
- Self-Protection – Makes evading properly configured DLPe protection a significant challenge.
Trellix’s Network DLP offering is really four solutions in a trench coat trying to sneak into an R rated spy movie:
- DLP Discover – a network share/cloud/database scanning solution that lets us encrypt and apply data labels to data stored in the network/select cloud locations.
- DLP Monitor – This appliance lets us watch the wire from a tap/SPAN port and catch any unencrypted data flows, as well as storing a copy of certain data protocols we can perform a retrospective lookback against (Capture).
- DLP Prevent for Email – This capability allows us to review the contents of outbound (and inbound if you’re paranoid about receiving data you wouldn’t like to) and, with the help of a suitable enforcement point such as Trellix EX, take action against any data exfiltration (Plus: Capture).
- DLP Prevent for Web – This capability allows us to review the content of web posts, or web pages, and make a policy-based access control decision thereupon (Plus: Capture).
The capabilities offered by Network DLP and DLPe all act to frustrate and disrupt our malicious insider, imposing access controls at every step of the way across a broad variety of exfiltration vectors, and even many obfuscation attempts.
HX, NX, PX, and IA all offer a key capability in protecting ourselves from insider threats: Packet Capture. When placed in-line, NX and PX offer event driven packet capturing abilities, and IA appliances offer full layer7 protocol analysis. HX with extensions can provide all sorts of forensic data to incident responders and security administrators. HX and NX are not just analysis tools, they allow administrators to react and take action against the very same IOCs they help to discover. These tools are absolutely critical to getting the information necessary to diagnose and stop exotic, sophisticated data exfiltration attempts. HX comes with self-protection capabilities to raise the roof on the difficulty of evasion.
Nothing can *eliminate* the risk of insider threats, but these countermeasures, properly deployed, configured, and governed, significantly increase the degree of planning, skill, luck, cooperation, and communication necessary to execute a successful insider data heist. Note that in order for this blueprint to work, the organization must be able to take an accurate data inventory, accurately categorize the sensitivity and classification level of the data worth protecting, and have an accurate picture of which groups of people should legitimately access each protected data pool.
TL;DR: Governance!

The one weird trick:
If you’ve made it this far, you definitely deserve to know the one thing you can do to make all of this much simpler to accomplish. Shockingly, a Trellix professional services consultant is about to recommend: Trellix Professional Services. We offer a variety of strategic and technical services that can help your team disrupt and obstruct intentional insider threats. Get in touch with your Trellix account manager, or if you haven’t got one yet, let us know you’re interested. Tell them you read this blog post, so they keep feeding me.
Additional reading:
- NIST SP 800-215 Guide to a Secure Enterprise Network Landscape
- NIST SP 800-192 Verification and Test Methods for Access Control Policies/Models
- NIST SP 800-111 Guide to Storage Encryption Technologies for End User Devices
- NIST SP 800-209 Security Guidelines for Storage Infrastructure
- NIST SP 800-210 General Access Control Guidance for Cloud Systems
- NIST SP 800-204 Security Strategies for Microservices-based Application Systems
- NIST SP 800-190 Application Container Security Guide
- NIST SP 800-201(Draft) NIST Cloud Computing Forensic Reference Architecture
- SP 800-207A, A Zero Trust Architecture Model for Access Control in Cloud-Native Applications in Multi-Cloud Environments
Make sure you read this disclaimer after all of that information:
RECENT NEWS
-
May 13, 2024
Seven Trellix Leaders Recognized on the 2024 CRN Women of the Channel List
-
May 6, 2024
Trellix Secures Digital Collaboration Across the Enterprise
-
May 6, 2024
Trellix Receives Six Awards for Industry Leadership in Threat Detection and Response
-
May 6, 2024
Trellix Database Security Safeguards Sensitive Data
-
May 6, 2024
92% of CISOs Question the Future of Their Role Amidst Growing AI Pressures
RECENT STORIES
The latest from our newsroom
Get the latest
We’re no strangers to cybersecurity. But we are a new company.
Stay up to date as we evolve.
Zero spam. Unsubscribe at any time.
