What Is Cyber Threat Hunting?
Cyber threat hunting is a proactive security search through networks, endpoints, and datasets to hunt malicious, suspicious, or risky activities that have evaded detection by existing tools. Thus, there is a distinction between cyber threat detection versus cyber threat hunting. Threat detection is a somewhat passive approach to monitoring data and systems for potential security issues, but it’s still a necessity and can aid a threat hunter. Proactive cyber threat hunting tactics have evolved to use new threat intelligence on previously collected data to identify and categorize potential threats in advance of attack.
Security personnel can’t afford to believe that their security system is impenetrable. They must remain ever vigilant for the next threat or vulnerability. Rather than sit back and wait for threats to strike, cyber threat hunting develops hypotheses based on knowing the behaviors of threat actors and validating those hypotheses through active searches in the environment. With threat hunting, an expert doesn't start from an alert or even Indicators of Compromise (IOC) but deeper reasoning and forensics. In many cases the hunter’s efforts create and substantiate the alert or IOC. Cyber threat hunting aggressively assumes that a breach in the enterprise has or will occur. Security personnel hunt down threats in their environment rather than deploy the latest tool.
Threat hunting investigations
Traditional cyber threat hunting is based on a manual process in which a security analyst scrutinizes data based on their knowledge of the network and systems to build assumptions about potential threats. Cyber threat hunting has advanced in effectiveness and efficiency through the addition of automation, machine learning, and user and entity behavior analytics (UEBA) to alert enterprise security teams of potential risks.
Once the risk or potential risk, as well as frequency of a hunt has been determined, an investigation is initiated. Examples of Cyber Threat Hunting investigations include:
- Hypothesis Driven Investigations: When significant information of a new, imminent threat vector is discovered, cyber threat hunting will delve deeper into network or system logs in search of hidden anomalies or trends that could signal the new threat. Analytics Driven Investigation: Searches based on information gathered from Machine Learning (ML) and Artificial Intelligence (AI) tools.
- Tactics, Techniques, and Procedures (TTP) Investigation: Hunting for attack mannerisms typically use the same operational techniques. This is helpful to source or attribute the threat and to leverage existing remediation methods that worked with these behaviors.
Threat hunting is specific to each environment, but some techniques can be applied to almost any environment. Core threat hunting techniques include:
Baselining
Baselining helps the hunter understand what “normal” looks like within an organization. SANS describes the value of baselining as looking for a needle in a haystack by removing the hay in double-digit percentages to shorten the time needed for the needle to become visible. To help minimize the time needed to combine baseline analysis with attacker technique, SANS suggests hunters consider the following questions:
- How prevalent is PowerShell in your environment?
- If prevalent, what does normal system administrator activity look like?
- Where does PowerShell activity typically come from, and what user accounts typically run it?
As a result, a hunter may not need to baseline all of PowerShell, but rather look for unexpected outliers or attacker-specific command structures.
Attack-Specific Hunts
Baselining aids the hunter in understanding the overall hunt environment, but attack-specific hunts can help track malicious activity faster. Attack-specific hunts typically focus on a specific threat actor or threat. However, the limits of their specific hunt model can throw off false positives. Attack-specific hunts combine with baselining often produce good results.
Time Sensitivity
All hunts are time sensitive, and therefore require hunters to validate their baseline terms periodically. SANS recommends confirming that new software implementations are not causing unnecessary traffic resulting in false-positive data. Keeping up with attackers’ shifting to new techniques – or reverting back to old techniques – require hunters to validate intelligence-based hunts and even hunt again if legacy techniques are detected.
Third-Party Sources
Hunting for needles in a data haystack can overwhelm teams of hunters. Third-party providers can help guide hunters to more successful hunts. SANS lists the following benefits hunters can gather from third-party sources:
- Ruling out false positive leads
- Focus on interesting leads
- IP lookups
- Geolocation
- Encrypted traffic metadata
- Log detection
- Attacker technique overlays
- Link analysis of internal vs. external or host vs. network data points
Five threat hunting steps
A cyber threat hunt is composed of steps or processes designed for an efficient, successful hunt. These steps include:
Step 1: Hypothesis
Threat hunts begin with a hypothesis or a statement about the hunter’s ideas of what threats might be in the environment and how to go about finding them. A hypothesis can include a suspected attacker's tactics, techniques, and procedures (TTPs). Threat hunters use threat intelligence, environmental knowledge, and their own experience and creativity to build a logical path to detection.
Step 2: Collect and Process Intelligence and Data
Hunting for threats requires quality intelligence and data. A plan for collecting, centralizing, and processing data is required. Security Information and Event Management (SIEM) software can provide insight and a track record of activities in an enterprise’s IT environment.
Step 3: Trigger
A hypothesis can act as a trigger when advanced detection tools point threat hunters to initiate an investigation of a particular system or specific area of a network.
Step 4: Investigation
Investigative technology, can hunt or search deep into potentially malicious anomalies in a system or network, ultimately determined to be benign or confirmed as malicious.
Step 5: Response/Resolution
Data gathered from confirmed malicious activity can be entered into automated security technology to respond, resolve, and mitigate threats. Actions can include removing malware files, restoring altered or deleted files to their original state, updating firewall /IPS rules, deploying security patches, and changing system configurations – all the while better understanding what occurred and how to improve your security against similar future attacks.
Threat hunting maturity model
An enterprise’s cyber threat hunting maturity model is defined by the quantity and quality of data the organization collects from its IT environment. An enterprise’s cyber threat hunting capabilities for hunting and responding, toolsets, and analytics factor into its threat hunting maturity model. The SANS Institute identifies a threat hunting maturity model as follows:
- Initial: At Level 0 maturity an organization relies primarily on automated reporting and does little or no routine data collection.
- Minimal: At Level 1 maturity an organization incorporates threat intelligence indicator searches. It has a moderate or high level of routine data collection.
- Procedural: At Level 2 maturity an organization follows analysis procedures created by others. It has a high or extremely high level of routine data collection.
- Innovative: At Level 3 maturity an organization creates new data analysis procedures. It has a high or extremely high level of routine data collection.
- Leading: At Level 4 maturity, an organization automates the majority of successful data analysis procedures. It has a high or extremely high level of routine data collection.).
Benefits of automation in cyber threat hunting
Modern adversaries are automating their techniques, tactics, and procedures to evade preventative defenses, so it makes sense that enterprise security teams can better keep up with attacks by automating their manual workloads. Incorporating automation benefits cyber threat hunting processes and helps SOCs better use their staff and resources. These include:
- Data Collections: Cyber threat hunting investigations involve collecting many categories and data from a variety of sources, requiring many hours to manually sort through and delineate good data from insufficient data. Automation can greatly reduce the amount of time required for collection and boost the valuable resources of security SOCs.
- Investigation Process: A seemingly constant volume of threat alerts and warnings can overwhelm even the most experienced and well-staffed SOC. Automation can reduce the threat noise by quickly categorizing which threats are high, medium, and low risk, thus reducing security staff time demands and allowing them to efficiently address those that need immediate action or further investigation.
- Prevention Process: Once a threat is identified, mitigations need to be created throughout an enterprise’s networks, endpoints, and cloud.
- Response Process: Automated responses can counter the smaller, more routine attacks, such as deleting customized script to isolate a compromised endpoint, deleting malicious files after isolation, and automatically using backup info to restore data compromised in an attack.
What’s required for cyber threat hunting?
What basic security resources does an enterprise need to activate threating hunting or in a threat hunting service?
Optimize Human Expertise Through Human Machine Teaming
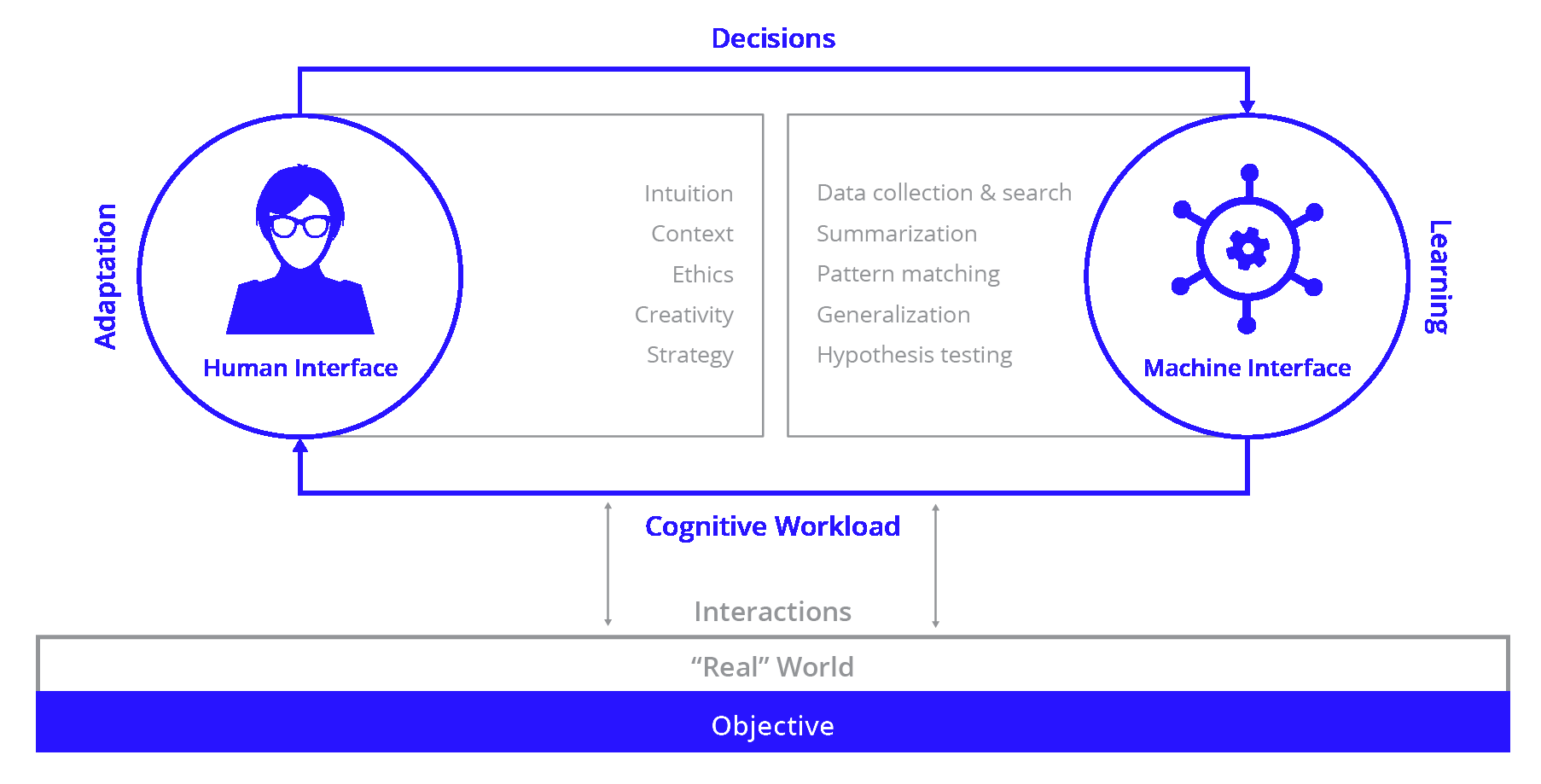
Never expect machines to be ethical or strategic. Never expect humans to be good at searching large volumes of data at speed and scale or perform complex pattern matching.
Human Hunters: Effective and efficient cyber threat hunting programs budget personnel and time for analysts to focus on hunting. Threat hunting requires human interaction and input to get to a resolution quicker with more accuracy. Knowledge of the threat landscape and the solid understanding of the IT environment, along with creative and intuitive thinking, are core fundamentals for a cyber threat hunter. Humans help get to a resolution quicker with more accuracy, and remove redundant and mundane manual errors that can be riddled with mistakes.
Organizational Model: Each organization must choose the most appropriate organizational model for its hunt team. Models are based on an organization’s size and budget along with the availability of analysts providing a diverse skillset. According to SANS: “Threat hunting entails a more mature organization with a defensible network architecture, advanced incident response capabilities, and security monitoring/security operations team.”
Tools & Technology: Many enterprises use comprehensive endpoint security solutions for detection to response and investigations, security monitoring, and management tools often used by threat hunters. These solutions can include:
- SIEM and statistical intelligence analysis tools, as SAS programs
- Threat Intelligence Providers (TIPS), and/or industry threat data banks. This expands to other items, such as the FSIAC (Financial Services Information Sharing and Analysis Center), for security data with actionable indicators.
- Bad IP address or hash, vulnerability management for published risks, and on-line reputable publications on threats.
Generally speaking, these technologies are siloed and require the cyber threat hunter to manually weave the value to decisive conclusion. This can be daunting for organizations that do not have the human expertise.
Data: Establishing a baseline of a network’s traffic or system behavior can then develop a baseline of expected and authorized events from which to identify anomalies. Use threat intelligence to focus on high-impact malicious activities first.