What Is Data Encryption?
Data encryption scrambles data into “ciphertext” to render it unreadable to anyone without the correct decryption key or password. Strong encryption solutions combined with effective key management protect sensitive data from unauthorized access, modification, disclosure or theft, and are thus a critical component of any security program. Data encryption can be employed both for data that is stored (“at rest”) and for data that is being transmitted or transported (“in motion”).
There are two main types of data encryption:
- Symmetric Encryption: With symmetric key algorithms, the same key is used to both encrypt and decrypt the data. This allows fast and efficient encryption and simpler key generation and management, but it is critical that the single key only be available to authorized users since that single key allows someone to access the data as well as to modify and re-encrypt the data without detection.
- Asymmetric Encryption: Asymmetric key algorithms use two mathematically related keys, a public key and a private key. The public key is used to encrypt the data, while a corresponding but separate private key is required to decrypt the data. One benefit of asymmetric encryption is that a more widely known public key can be used to encrypt data, but only those with the private key can decrypt and access the data.
What are data encryption solutions?
A data encryption solution is a software system that employs data encryption algorithms to protect sensitive data, combined with management tools for deploying and monitoring data encryption across an organization. Encryption solutions can also provide tools for key management to ensure keys, passwords and other information needed to encrypt or access data are available only to authorized users and are changed or revoked based on defined policies.
Most organizations protect their information with traditional security products such as firewalls, intrusion prevention, and role-based access control applications. These all help prevent data breaches. However, when attackers successfully breach a network—and they inevitably do—data encryption software is the critical, last defense against the theft and exposure of sensitive data.
Most government and industry regulations, such as those protecting consumer privacy and financial data, require organizations to use data encryption tools. Non-compliance can result in stiff penalties. Conversely, use of a strong data encryption solution can protect an organization if a data breach occurs or a laptop is stolen.
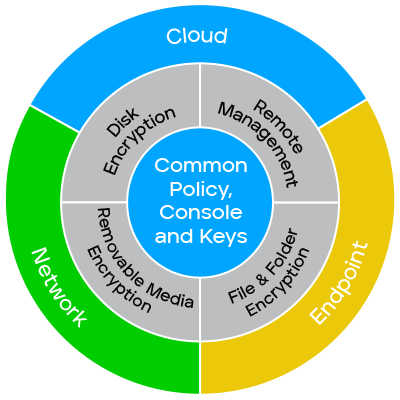
Key features of a data encryption solution
Two important aspects of data encryption tools are usability and scalability. The data encryption software must be convenient for employees to use—or they won’t use it—and scalable to accommodate an organization’s growth and changing security needs.
Below are additional important capabilities to consider when evaluating a data encryption solution.
Strong encryption standards. Government agencies and private and public organizations around the globe use the industry standard for encryption: the Advanced Encryption Standard (AES)-256. AES replaced the older Data Encryption Standard (DES), which had become vulnerable to brute force attacks, which occur when an attacker tries multiple combinations of a cipher until one of them works. The two well-known certification processes for encryption products or implementations are:
- The National Institute of Standards and Technology (NIST) Federal Information Processing Standard (FIPS) 140-2, which is a U.S. government computer security standard
- The Common Criteria for Information Technology Security Evaluation, which is an internationally supported certification standard and program
Encryption of static and dynamic data. Static data, or at-rest data, is saved on servers, desktops, laptops, etc. Static data is encrypted either by the file, the folder, or the entire drive.
Dynamic data, or in-motion data, travels over a network or the internet. Email is the most common example. Dynamic data can be protected in two ways:
- Encrypt the transmission using network encryption protocols, such as internet protocol security (IPsec) and transport layer security (TLS), to establish a secure connection between endpoints
- Encrypt the message and its payload, which ensures that only an authorized recipient can access it
Granular encryption. While it’s possible to encrypt all data, this can strain IT resources. Instead, most organizations encrypt only the most sensitive data, such as intellectual property and personally identifiable information, like social security numbers and bank account information.
Data encryption tools offer differing levels of granularity and flexibility. Common options include encryption of specific folders, file types, or applications, as well as whole drive encryption and removable media encryption. Full disk encryption is frequently used for laptops, which can be lost or stolen. Encryption of laptops, tablets, and removable media may protect an organization from liability if the device is stolen.
Key management. Data encryption software has key management capabilities, which include creating, distributing, destroying, storing, and backing up the keys. A robust and automated key manager is important for quick and seamless encryption and decryption, which in turn is critical to the smooth operation of the organization’s applications and workflows.
Enforcement of encryption policies. Encryption policies define how and when data is encrypted. A data encryption solution with policy management features enables IT to create and enforce encryption policies. For example, consider the case of an employee attempting to save a confidential file to a removable USB drive to use it to work from home. The encryption software sends the employee an alert that this action violates a data security policy and blocks the employee from copying the file until it is encrypted. Automated enforcement can ensure that data security policies are followed.
Always-on encryption A useful feature for ensuring that sensitive files stay encrypted is “always-on” encryption, which follows a file wherever it goes. Files are encrypted when created and remain encrypted when they are copied, emailed, or updated.
Unified encryption management. IT departments must often contend with pre-existing encryption technologies in their organizations. For example, a newly acquired business unit may use its own encryption technology, or a department may use native encryption that is part of Apple and Microsoft products, like FileVault on OS X or BitLocker on Windows. For this reason, some data encryption solutions support unified management of multiple technologies.
A unified management console also provides visibility into all endpoints, including a record of each device’s encryption usage. This can avoid non-compliance penalties if a laptop is lost or stolen.
On-premises or cloud-based encryption?
An organization can’t assume that a cloud provider will automatically provide encryption as part of a cloud application or infrastructure service. Encryption uses extra bandwidth and CPU resources, increasing a cloud provider’s costs, so most providers don’t include encryption or offer only partial encryption. In general, encrypting the data is the customer’s responsibility.
The best cloud encryption strategy includes end-to-end encryption of the connection and of any data that is uploaded to the cloud. In these models, cloud storage providers encrypt data upon receipt, passing encryption keys to the customers so that data can be safely decrypted when needed. Organizations can pay for an end-to-end encryption service or encrypt data on-premises before it is uploaded to the cloud.
Data encryption software is one of the most effective forms of data security, when accompanied by secure encryption key management and data loss prevention best practices. Data encryption tools offer strong encryption of corporate and user endpoints and shared services, protecting valuable corporate data and providing centralized management of encryption policies.