Ransomware Detection and Response
Put ransomware nightmares to sleep. Minimize the time to detect, investigate, and respond to ransomware threats.
The ransomware challenge
Ransomware is not an if but a when. The Trellix Advanced Research Center analyzed more than 9,000 real-world attacks to develop a ransomware kill chain model that helps you combat ransomware while reducing time to value, cost, complexity, and overall risk.
Addressing all stages of the ransomware kill chain
Trellix provides critical coverage for all stages of a sophisticated ransomware campaign – from reconnaissance to recovery.


![]()
Reconnaissance
Prepare for an attack with insights, services, and threat intelligence.

![]()
Initial access
Prevent attackers from gaining access and detect suspicious activity on email and endpoints.

![]()
Escalation and lateral movement
Detect attacker activity with visibility into lateral movement, use of remote management tools, and more.

![]()
Data collection and exfiltration
Mitigate potential impact by preventing data loss and providing visibility into data archiving and other activities.

![]()
Degradation of recovery and system security services
Mitigate malicious tampering of files, services, and security settings and detect any destruction of data.

![]()
Ransomware deployment, execution, and encryption
Recover with rollback actions, guided playbooks, and enhanced visibility.

![]()
Recovery and retrospective
Perform root cause analysis, so that you avoid reinfection and emerge stronger and more resilient.
The Trellix advantage
- Strengthen Posture
Trellix’s comprehensive, integrated, and open AI-powered and XDR reduce overall ransomware risk. - Minimize Time to Detect
VAutomatic multi-vector, multi-vendor correlation and contextualization reduce Mean Time to Detect (MTTD). - Reduce Time to Investigate and Respond
AI-guided investigation, response, and playbooks reduce Mean Time to Investigate (MTTI) and Respond (MTTR). - Empower Talent
Trellix Professional Services augment your team and help you shore up defenses and recover faster. - Reduce Costs
Simplified security operations, increased productivity, and faster time to value reduce overall costs. - Enrich with Threat Intelligence
Embedded in the platform and available as a service, threat intelligence uncovers and prioritizes threats.
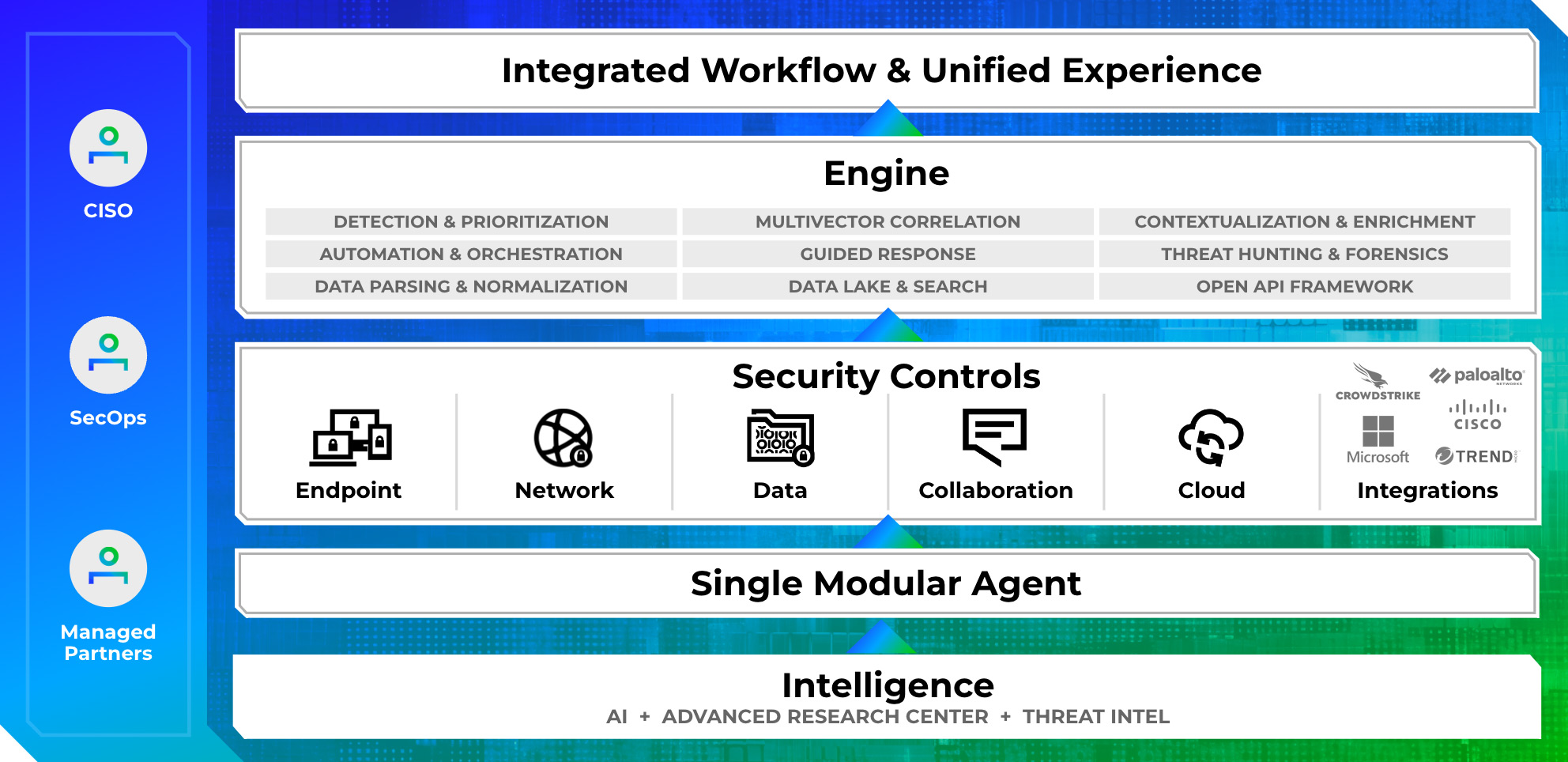
Stay secure with the Trellix Platform
Stop ransomware in its tracks with Trellix's XDR platform, industry-leading security controls, and services – powered by Trellix Wise.
E-book
The CISO's Guide to Ransomware
How to prepare your organization to take action when every minute counts. Communicate with your board more effectively, evolve your maturity, and learn 10 best practices to become ransomware ready.
Get the E-book