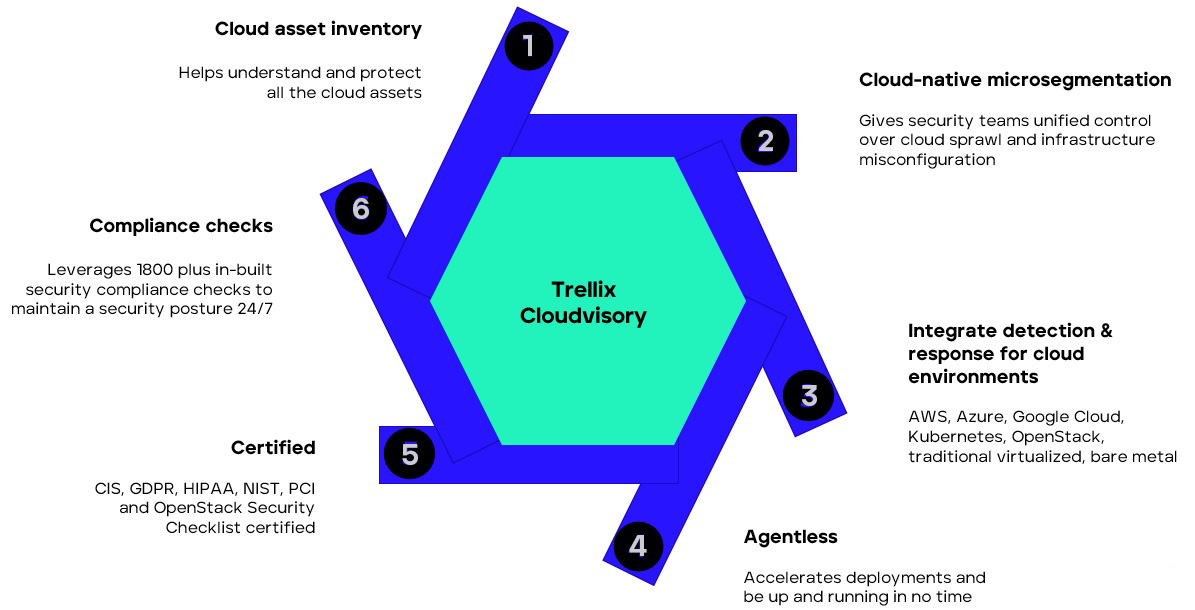
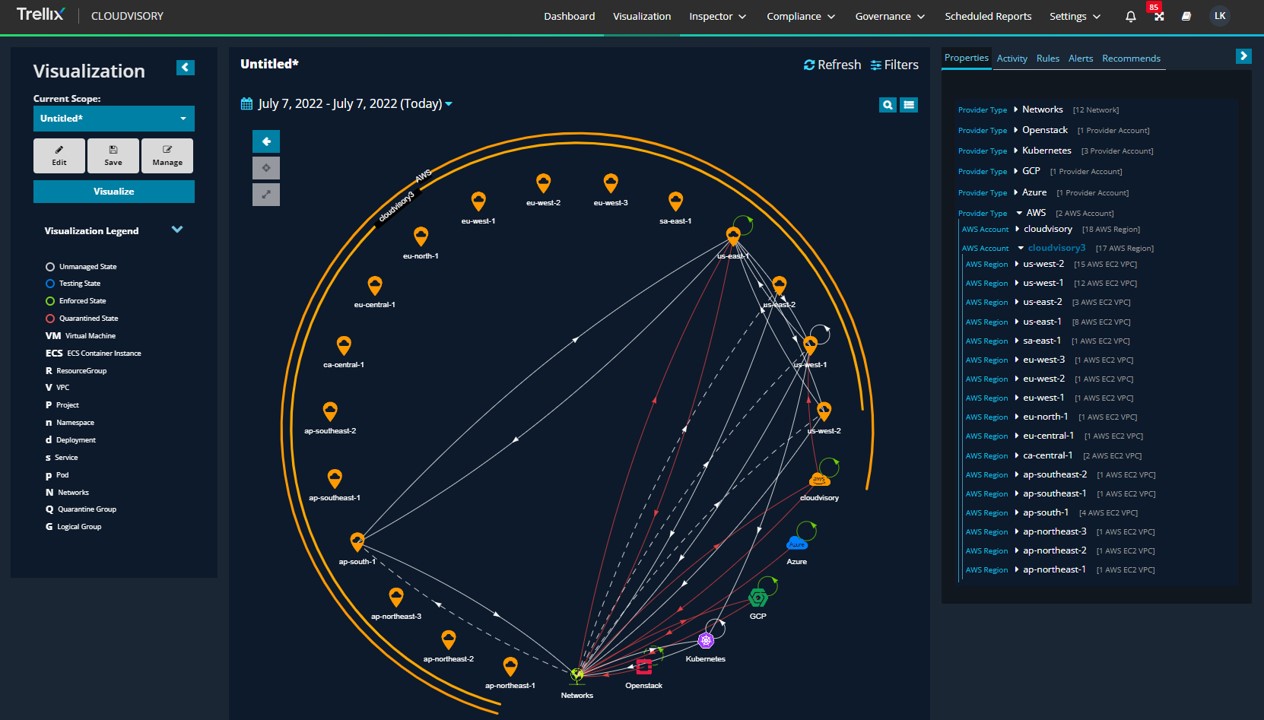
Trellix Cloudvisory
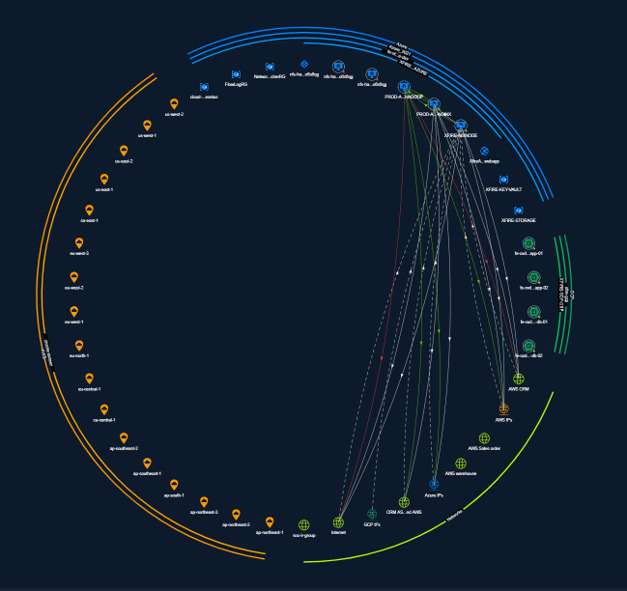
A centralized command center for managing multi-cloud environments and workloads.
Product Tour
Features
Terraform API’s
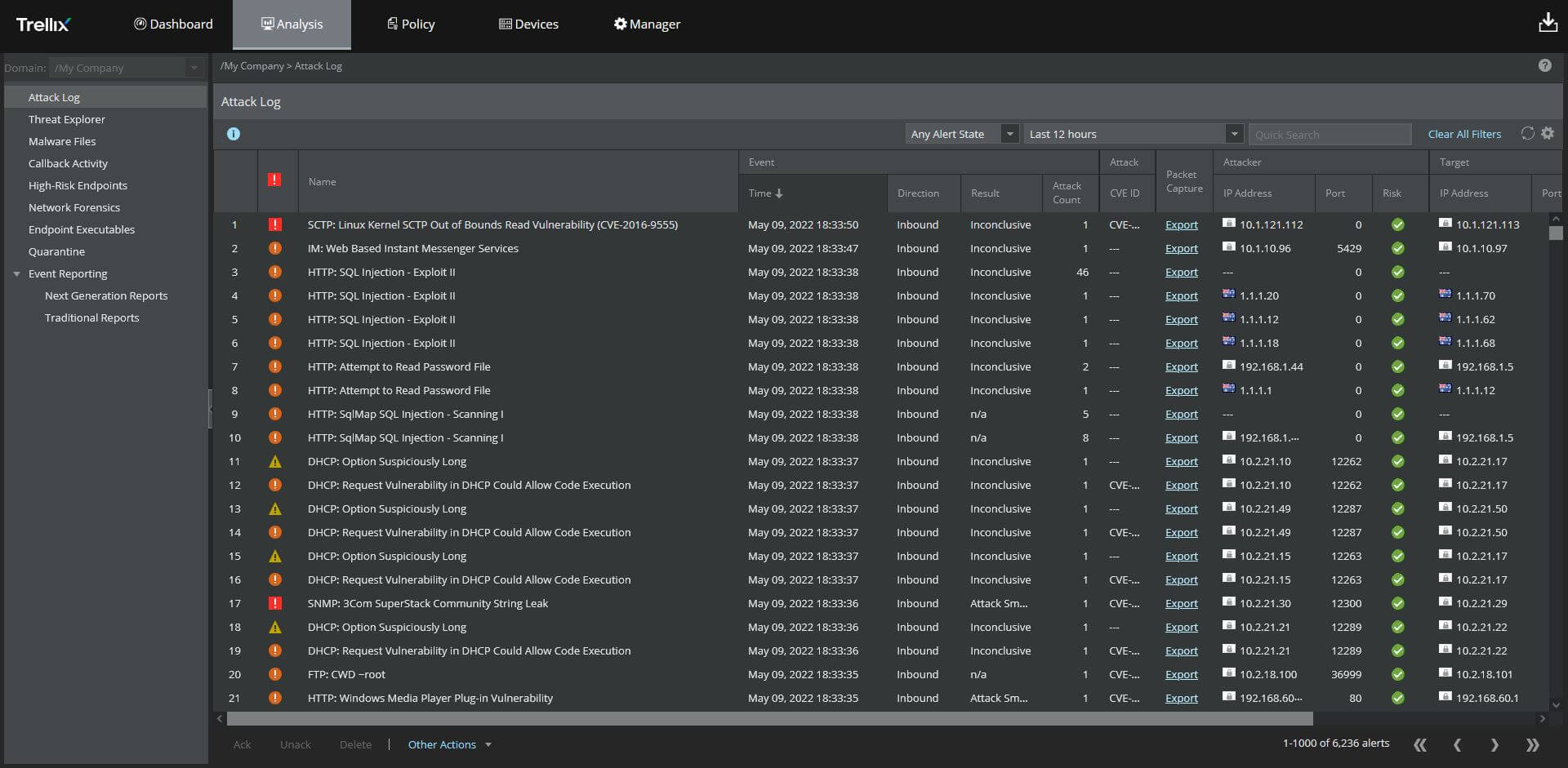
Identify and address vulnerabilities early in the process before vulnerabilities and misconfigurations impact infrastructure
No mis-configurations
Run continual assessments to ensure that processes are secure and do not drift from the original configurations
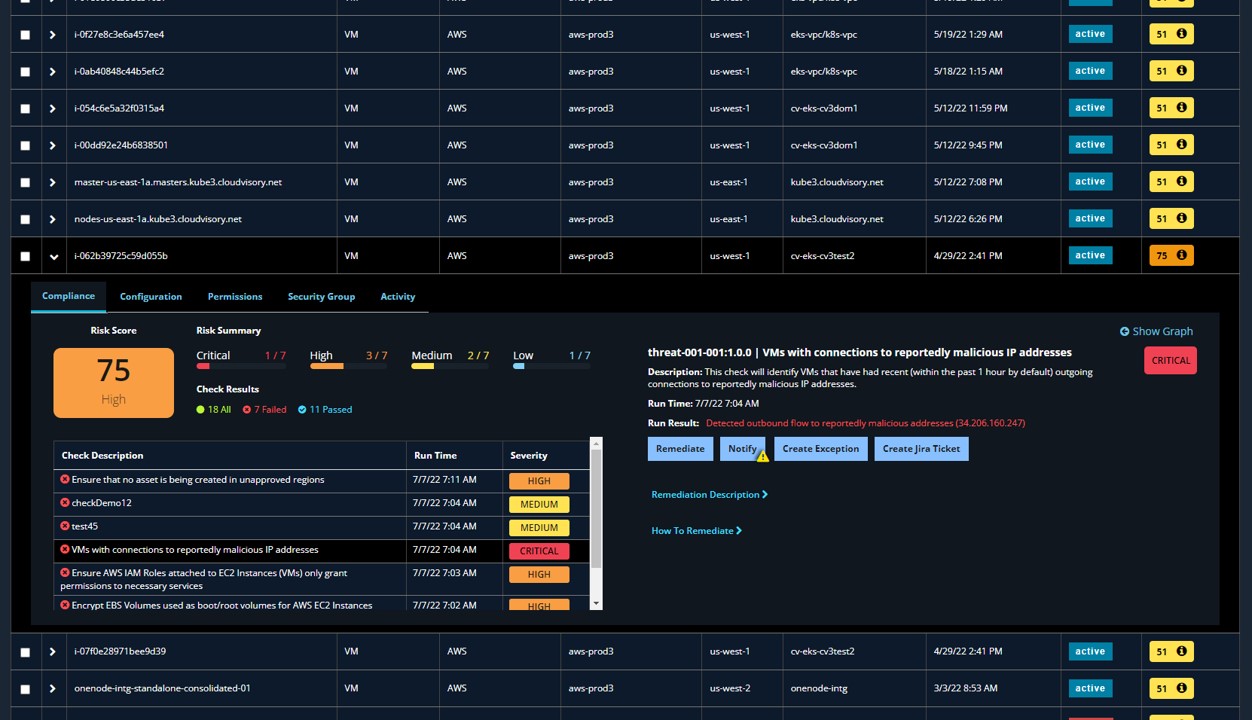
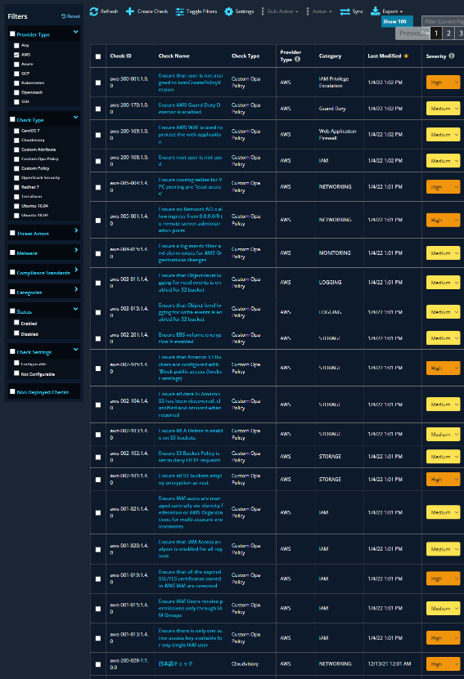
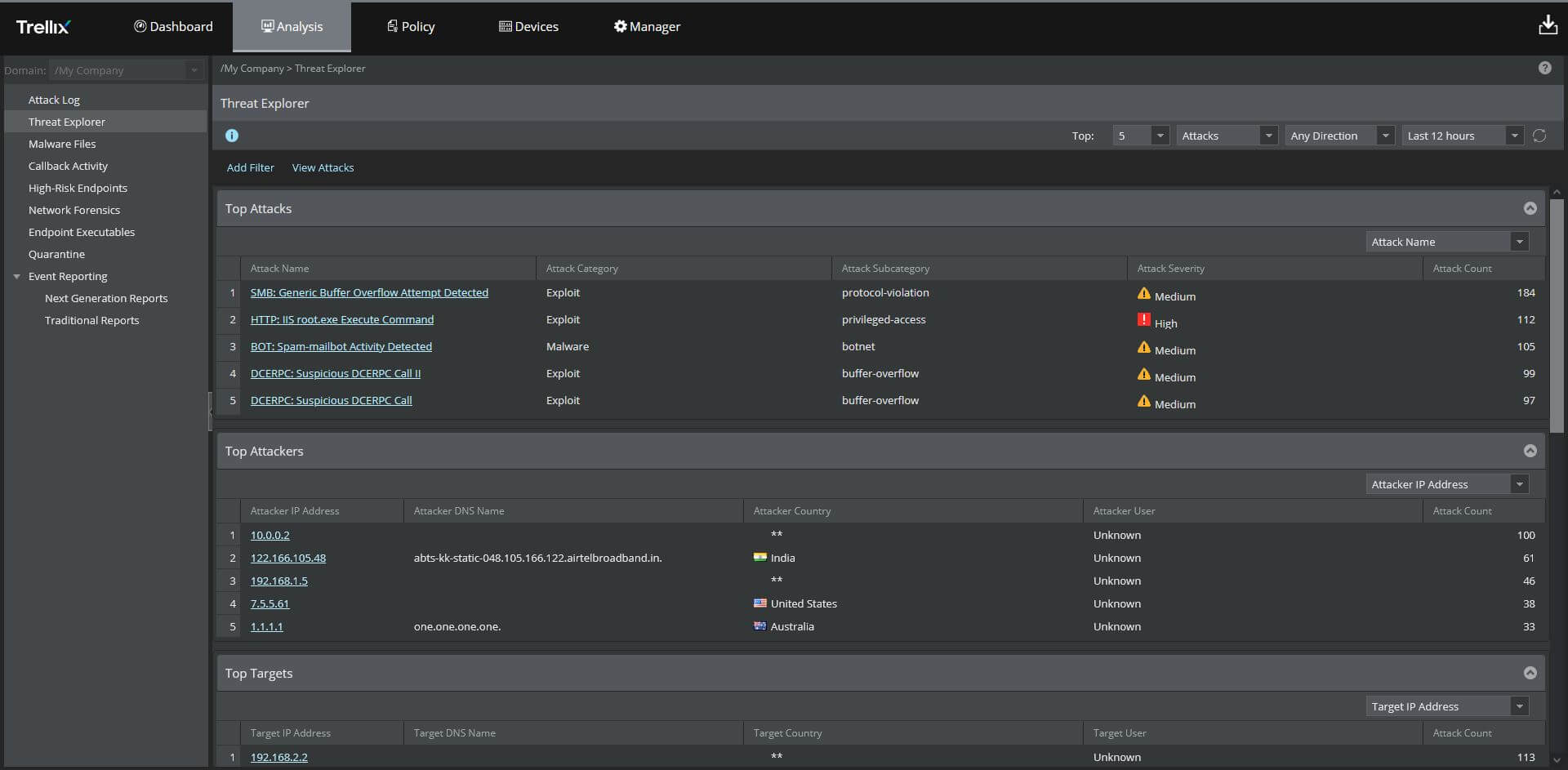
Asset inventory inspector
Drills down to granular level on a per asset basis and shape them further
Policy inspector
Forensic investigator to help map users and resources access for IAM policies
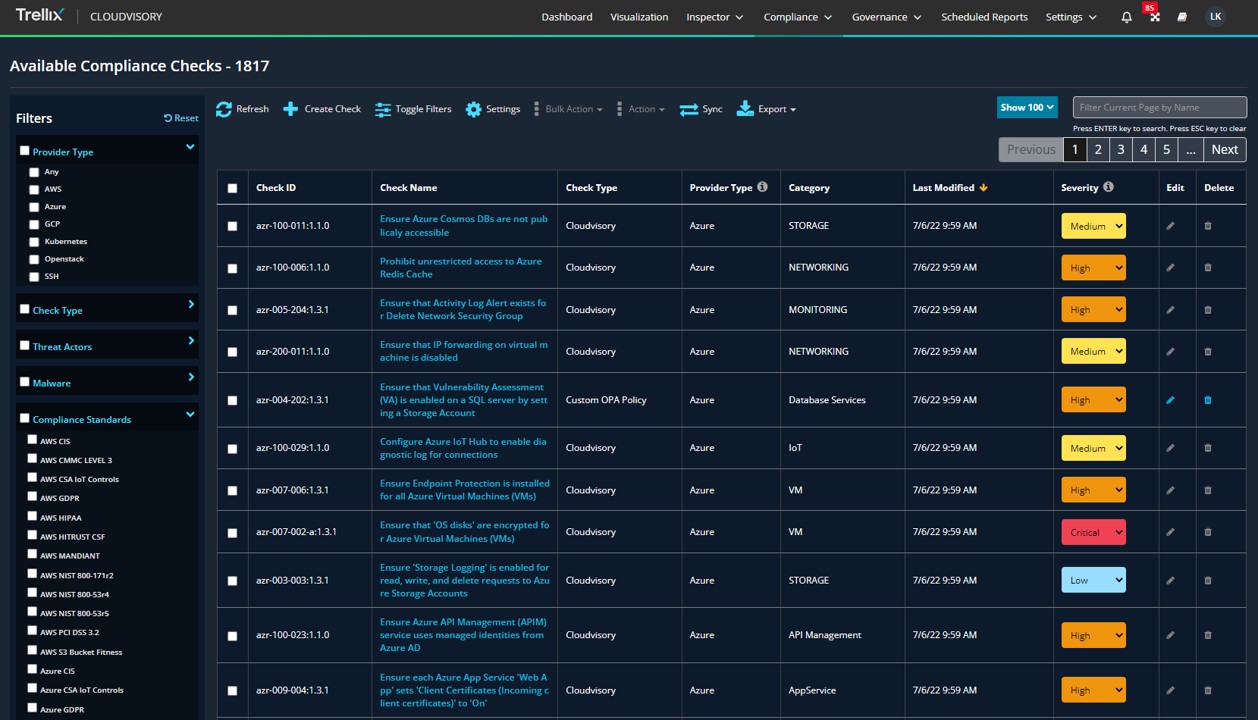
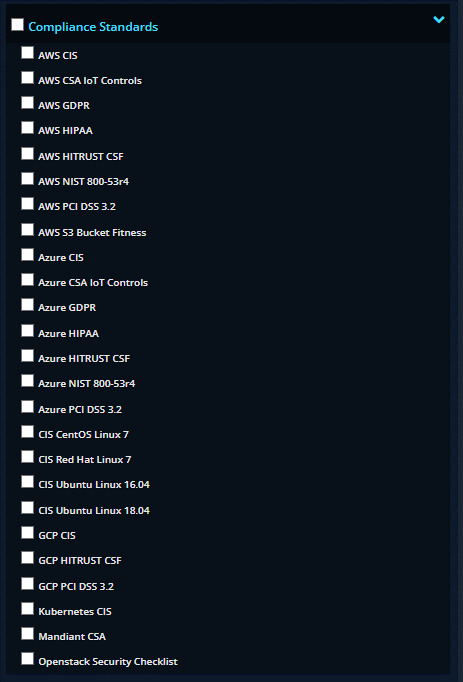
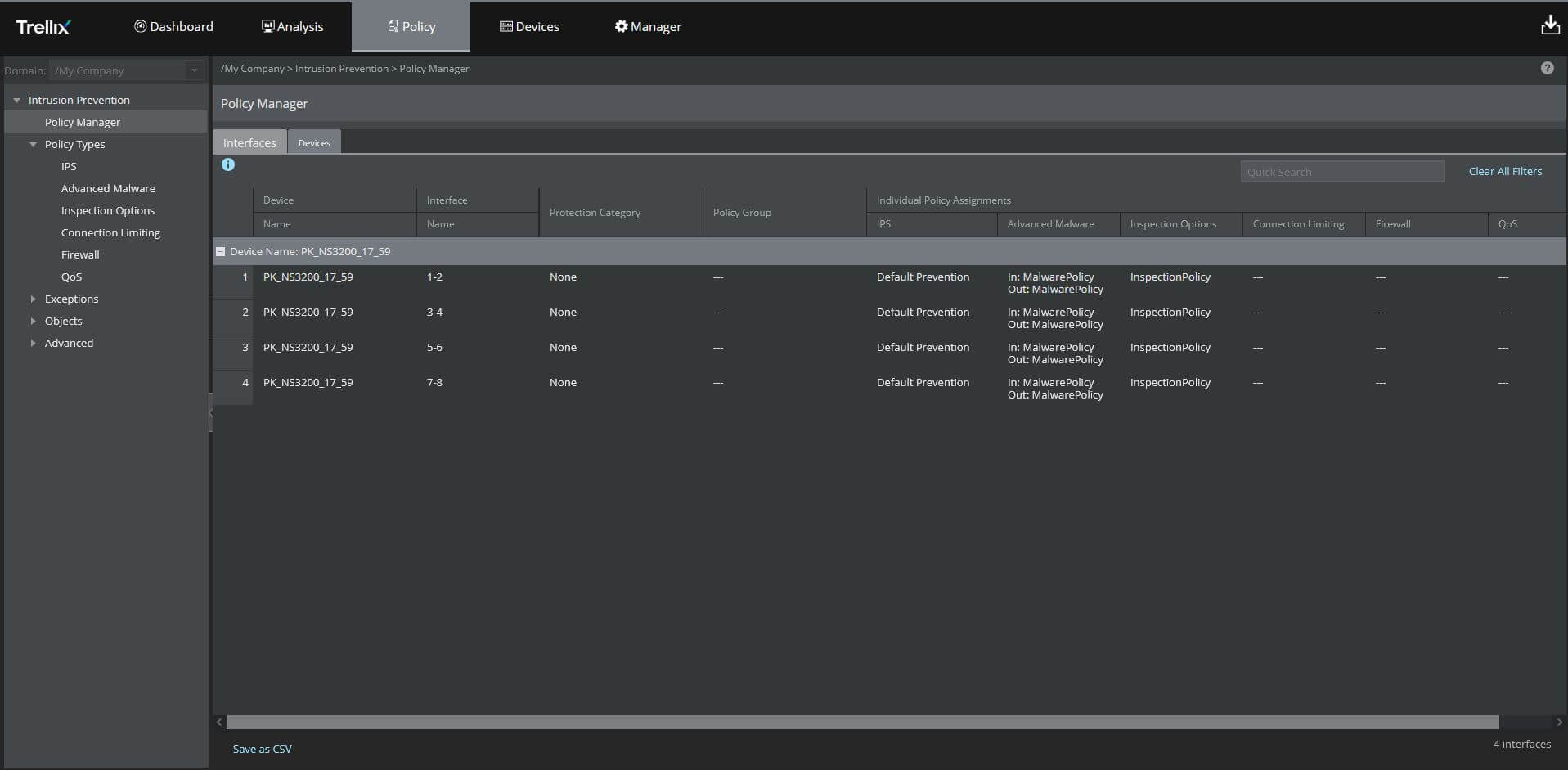
Compliance check inspector
GDPR, HIPPA, NIST, PCI, S3 Bucket fixes
Playbooks
Cloud-native remediations with customizable workflows/playbooks for business processes.