Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
The Bug Report – July 2023 Edition
By Trellix · August 02, 2023
This story was also written by John Dunlap.
Why am I here?
Summer is now in full swing, and our July Bug Report is similarly coming out swinging. This month comes with a red-hot list of software vulnerabilities being used in the wild in attack campaigns seeking to melt your secure environment like an ice cream cone sitting in direct sunlight.
Without further ado, our “fresh off the grill” vulnerabilities for this month are:
CVE-2023-36884: A summer STORM is brewing....
What is it?
Another month and another serious Office bug. However, CVE-2023-36884 is especially dangerous as it is being widely exploited by APT group STORM-0978 to infect victim hosts with ransomware and to conduct extortion attacks. Stealthier installations of "RomCom", a backdoor associated with Russian state sponsored attacks against Ukraine, have also been observed. As the attack was both widespread and dangerous, targeting companies for industrial espionage and ransomware across the world, Microsoft threat intelligence published a blog on the attacks. Attacks utilizing CVE-2023-36884 appear to originate from Russia, and unsurprisingly appear to target organizations with ties to Ukraine. This includes obvious targets such as the Ukrainian World Congress, but also organizations with ties to Ukraine that are less obvious, such as American financial institutions doing business in Ukraine. Telecommunications companies have also been targeted.
Who cares?
Considering the checklist of people who should care includes organizations that 1) use Microsoft’s Office Suite and 2) don’t enjoy being ransomed by cybercriminals—then a whole lot of people should care. For those companies that do any business in Ukraine or with Ukrainian partners whatsoever, they should take this vulnerability especially seriously.
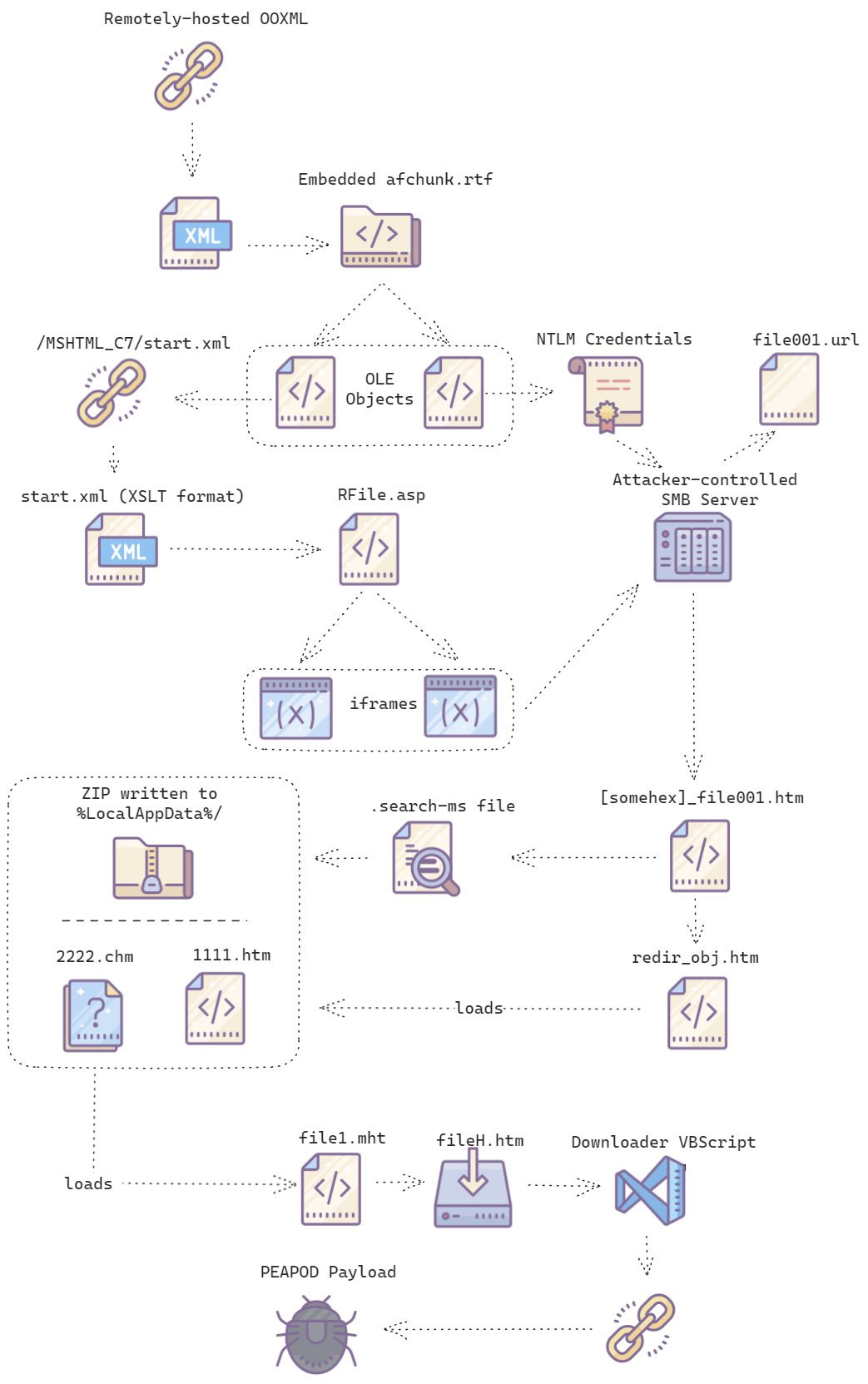
Threat researcher Paul Rascagnères published a graphic (made by his colleague, senior threat intelligence analyst Charlie Gardner) demonstrating the observed routes of infection—which we’ve included below for ease of reference. As this vulnerability has been widely exploited in the wild, potentially impacted organizations should review this graphic closely, as well as Microsoft’s blog post for potential indicators of compromise.
What can I do?
This is the part where we would normally tell you to update Windows immediately, but as of 7/24/2023 Microsoft lists this vulnerability as “remediation unavailable.” With no effective remediation for the vulnerability right now, the situation is a little more hopes and prayers than we’d like.
However, there are several mitigation strategies available for potentially affected organizations. We’ve included a list below of those suggested by Microsoft:
- Ensure that defender for Office 365 is activated, as it detects several stages of the malware.
- Ensure that safe attachments and safe links protection options are enabled.
- If you use Microsoft 365 Apps Versions 2302 and later, you are protected from the vulnerability.
- Use the “Block all Office applications from creating child processes attack surface reduction” Attack Surface Reduction (ASR) rule as described here.
- Set the FEATURE_BLOCK_CROSS_PROTOCOL_FILE_NAVIGATION registry key as described here.
CVE-2023-3519: Gateway to Vulnerability

What is it?
We normally think of gateway devices as hardened barriers to entry for our network. Connoisseurs of edge device vulnerabilities will know that this is often not the case, but situations like CVE-2023-3519 are a whole new level of bad. The last thing we want from a Citrix gateway is unauthenticated remote code execution, but somehow that’s what we’re getting regardless.
Worse yet, the vulnerability has been exploited in the wild. While there are no public proof of concept exploits, scanners are on GitHub, which imply that less skilled attackers are attempting massive scans for vulnerable devices. Even more, threat intelligence researchers have reported PHP webshells being found on infected endpoint devices—further confirming that the vulnerability is easy to exploit.
Who cares?
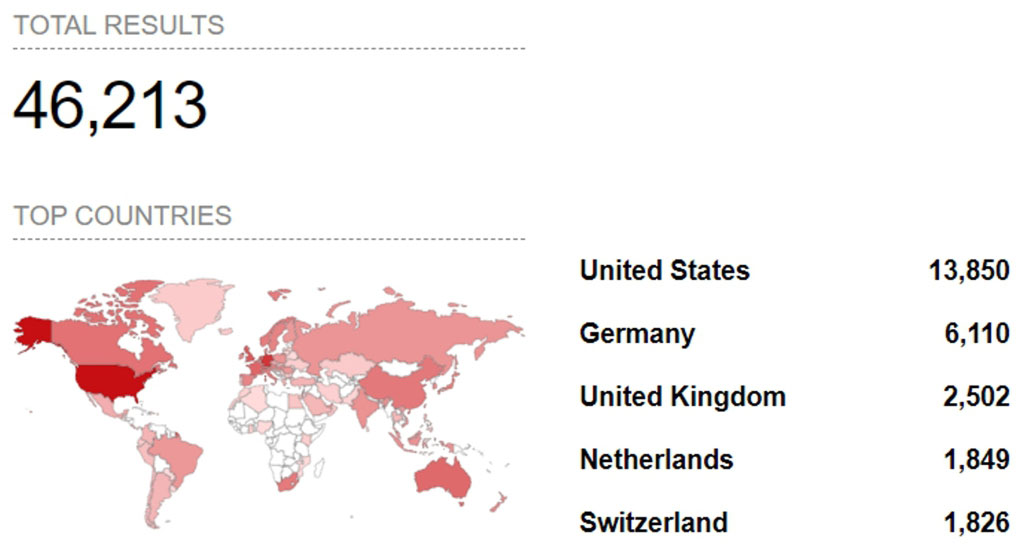
According to Citrix, the vulnerability is only exploitable if you have the device configured as a Gateway. However, a quick search on Shodan reveals that this Gateway configuration is commonly used for thousands of Citrix devices.
Any organization with any of the following Citrix (formally NetScaler) devices configured as Gateways should care a lot about this vulnerability:
- NetScaler ADC and NetScaler Gateway 13.1 before 13.1-49.13
- NetScaler ADC and NetScaler Gateway 13.0 before 13.0-91.13
- NetScaler ADC 13.1-FIPS before 13.1-37.159
- NetScaler ADC 12.1-FIPS before 12.1-55.297
- NetScaler ADC 12.1-NDcPP before 12.1-55.297
What can I do?
In this case, the only thing you can do is apply the update distributed by Citrix here.
However, this vulnerability is known to drop common webshells that can be investigated for any potential compromise. A list of compromised files commonly associated with this vulnerability is shown below:- alfav3-encoded.php
- alfav4.1-decoded.php
- alfav4.1-encoded.php
- andela.php
- bloodsecv4.php
- obfuscated-punknopass.php
- punk-nopass.php
- punkholic.php
- r57.php
- smevk.php
- TwemlowsWebShell.php
- wso2.8.5.php
- insight-new-min.js
- info.php
- by.php
- c99ud.php
- cmd.php
- configkillerionkros.php
- mini.php
- prod.php
- log.php
- logout.php
- vpn.php
- config.php
- shell.php
- poc.php
- rshell.php
- php-reverse-shell.php
CVE-2023-29298: Yet Another ColdFusion Vulnerability
What is it?
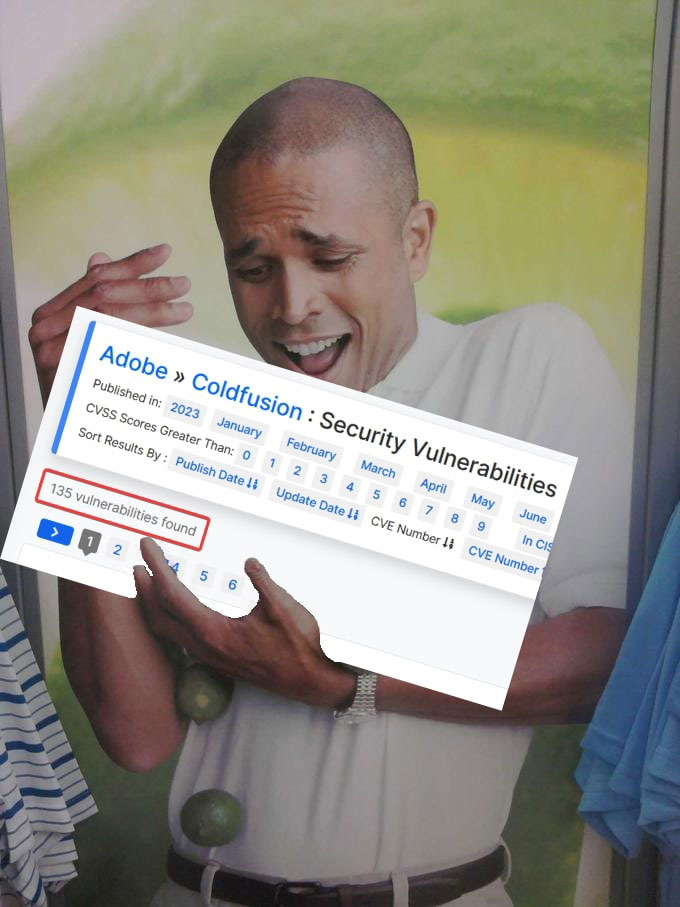
While Adobe has described ColdFusion as “battle-proven," ColdFusion has had just a small handful of vulnerabilities over the years.
The definitely not notoriously vulnerable web application programming framework was found to have what amounted to an authorization bypass in CVE-2023-29298, where attackers were able to gain access to administrative “CFM” endpoints. This in turn allowed them to gain remote code execution with CVE-2023-38203, a deserialization vulnerability in the handling of WDDX packets.
Who cares?
Anyone running ColdFusion should be aware of this vulnerability and the (very likely) possibility of further vulnerabilities in the future. The following specific versions are considered vulnerable to the exploit chaining together CVE-2023-29298 and CVE-2023-38203:
- ColdFusion 2018 Update 16 and Earlier
- ColdFusion 2021 Update 6 and Earlier
- ColdFusion 2023 GA Release (2023.0.0.330468)
A Shodan search displays about 3,000 hosts (at the time of writing) that can be definitively marked as using ColdFusion. However, there may be more vulnerable hosts, as evidence of ColdFusion does not always show up in HTTP headers. ColdFusion is also often used in corporate intranets.
It should also be noted that while CVE-2023-38203 has been effectively remediated, it appears CVE-2023-29298 itself has only been partially mitigated with the available patches.
What can I do?
While Adobe was able to patch the remote code execution bug (CVE-2023-38203), as of this writing, the authorization issue is still being remediated. As there is little the attackers are able to do with CVE-2023-29298 without the presence of CVE-2023-38203, this seems pretty reassuring in solving the problem. But it’s not.
If attackers discover a way to bypass the remediation for CVE-2023-38203, which is in itself a bypass of the previously known vulnerability CVE-2023-29300, then the system will be vulnerable to remote code execution once again. As the deserialization of WDDX messages is a core component of ColdFusion, issues of this nature are highly likely to reoccur, as the core technology at the root of vulnerability is extremely difficult to remove from the product.
Can we suggest replacing Adobe ColdFusion with one of the many alternatives that are less vulnerable to RCE exploits?
RECENT NEWS
-
May 13, 2024
Seven Trellix Leaders Recognized on the 2024 CRN Women of the Channel List
-
May 6, 2024
Trellix Secures Digital Collaboration Across the Enterprise
-
May 6, 2024
Trellix Receives Six Awards for Industry Leadership in Threat Detection and Response
-
May 6, 2024
Trellix Database Security Safeguards Sensitive Data
-
May 6, 2024
92% of CISOs Question the Future of Their Role Amidst Growing AI Pressures
RECENT STORIES
The latest from our newsroom
Get the latest
We’re no strangers to cybersecurity. But we are a new company.
Stay up to date as we evolve.
Zero spam. Unsubscribe at any time.