Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
The Bug Report — August 2022 Edition
By Philippe Laulheret · September 7, 2022
Your Cybersecurity Comic Relief

Why am I here?
Indeed, why are we here? School is back in session, there’s a chill in the air that says fall is around the corner, but before we say goodbye to the last days of summer, let’s revisit some of the most striking bugs of August 2022:
- CVE-2022-36804: Atlassian Bitbucket Server and Data Center
- CVE-2022-0028: PAN-OS
- Unassigned: YARA
- CVE-2022-38392: Certain 5400 RPM hard drives
First, a vulnerability in source code repository service Bitbucket leaves the lid open to arbitrary code execution. Next, Palo Alto firewalls are under fire (ah!) for being actively exploited to cause havoc. Then, a “secret” vulnerability in YARA that may have flown under the radar if it weren’t for the constant surveillance of internet sleuths (and of course, the French!). Finally, a blast from the past as Janet Jackson’s Rhythm Nation is making the news for breaking hard drives of yore. So, let’s dig in!
CVE-2022-36804: Don’t put all your bits in the same bucket
What is it?
CVE-2022-36804 is a command injection vulnerability that affects Bitbucket Server and Data Center. The vulnerability can be exploited if the server exposes a public repository (or if an attacker has read access to a private repository) and leads to arbitrary code execution. As always, watch out who you share your private bits with!

Who cares?
Bitbucket is widely used as a Git-based code hosting platform, and both the Bitbucket Server and Bitbucket Data Center are affected. Though not as big as GitHub, Bitbucket boasts over 10 million users and 28 million repositories on its cloud platform alone and has become increasingly popular in enterprise spaces since its acquisition by Atlassian. Odds are, if your org uses JIRA or Confluence, it probably uses Bitbucket, too. Fortunately, cloud users (via bitbucket.org) are not affected. Your private bits are safe in the cloud!
What can I do?
If you’re using either of the vulnerable products, make sure you patch promptly as the security researcher who reported the flaw announced they would release a proof of concept by late September. Atlassian also suggests a couple of mitigations like stop sharing your repositories publicly (via feature.public.access=false) until you are able to deploy the patch. Bear in mind this isn’t a full mitigation as people having read access to your private repositories may still be able to perform the attack.
CVE-2022-0028: With one snap of the finger from attackers, PAN-OS might take half of the internet down. Well, almost.*

* Necessary disclaimer, this title is a pun, not a statement on what PAN-OS can or cannot do. Please don’t hassle our legal department.
What is it?
CVE-2022-0028 is a reflected and amplified DoS affecting PAN-OS. In plainer English, this means vulnerable systems could be leveraged to conduct DoS against third parties (the reflected part) and it requires little volume of data from the attacker (the amplified part) to conduct the attack. More worryingly, this vulnerability has been flagged by CISA for being actively exploited.
Who cares?
Users of smart pans (and smarty pants, such as yours truly) are safe as PAN-OS is not deployed on those. Instead, the vulnerability affects a wide gamut of Palo Alto firewall appliances and VMs. However, the vulnerability requires a non-standard configuration to be exploitable, so you might be fine unless you botched it. As Palo Alto puts it, “To be misused by an external attacker, the firewall configuration must have a URL filtering profile with one or more blocked categories assigned to a security rule with a source zone that has an external facing network interface. This configuration is not typical for URL filtering and, if set, is likely unintended by the administrator.”
What can I do?
If you’re the proud owner of a Palo Alto firewall, keep it happy by ensuring its firmware is up to date. And while you’re at it, if you rely on its URL filtering capabilities, double check the configuration as it seems the vulnerable scenario comes from a misconfiguration, that may be frequent enough for threat actors to adopt this vulnerability into their attacker playbook.
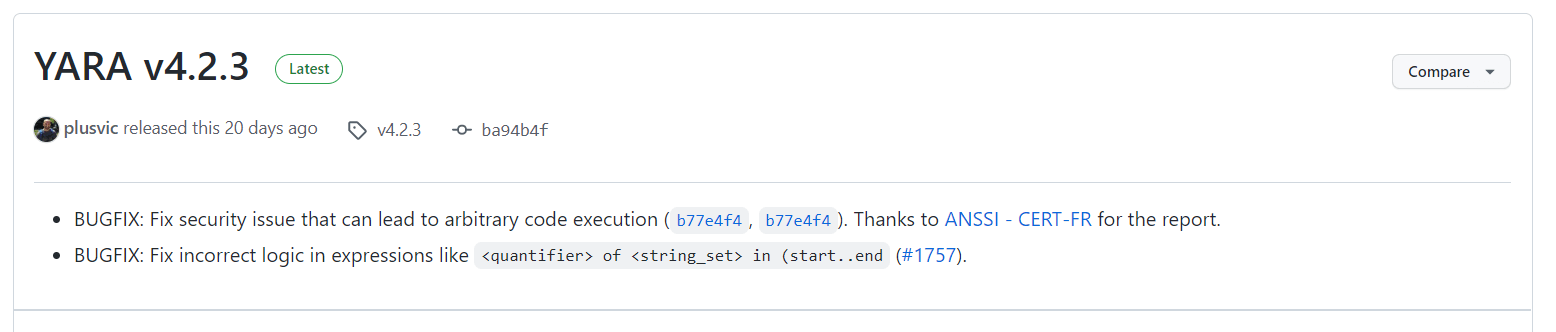
NO CVE! But a GitHub issue and a new version of YARA.
What is it?
No CVE or CVSS rating for this bug, but it’s definitely a security vulnerability as flagged by these release notes. The French ANSSI reported a potential arbitrary code execution affecting YARA which got fixed in release 4.2.3. Pardon my French, but ooh la la!
Who cares?
As there’s very little information available about the exploitability of the bug or how it can be reached, it’s hard to tell. That being said, it’s important to recall, YARA plays a crucial role in the industry to support threat hunting and malware analysis. So, if you’re into parsing untrusted and known malicious input and like to keep your infrastructure from being exploited by the data you scan, then maybe you should care, even just a little.
What can I do?
Launch YARA from the command line with the -v flag; if it spits out a number smaller than 4.2.3, it means you need to update to the 4.2.3 release linked above (or newer) ASAP. While you’re at it, make sure your friends in the industry who might be relying on the tool are aware an important security update was released.
CVE-2022-38392: My hard drive is vibing way too hard to that song
What is it?
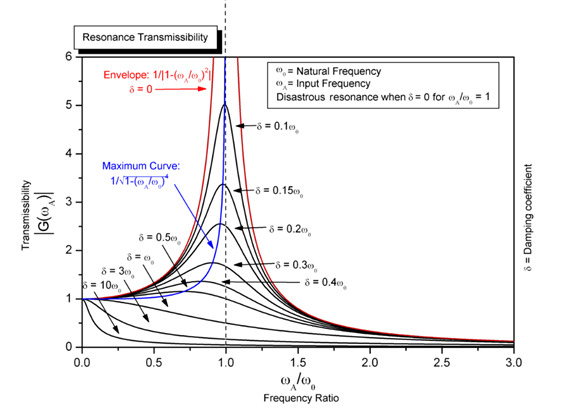
This month, we’re ending on a vuln that isn’t exactly critical, but nonetheless fascinating (and hilarious): CVE-2022-38392. With a whooping 5.8 CVSS score, some unnamed hard drives that likely nobody uses anymore are vulnerable to a DoS attack. The PoC, widely available on your favorite audio streaming platform, was (likely?) not designed to attack the device, but happens to trigger the fault, nonetheless. If you’re bold enough to try it on your own machine, feel free to play Janet Jackson’s “Rhythm Nation” as a musical background to this blog, and see if your computer self-destructs (spoiler alert: it won’t). A patch has been available for decades; a software one mind you, as patching the law of physics is not yet something one can do. There used to be an urban legend that opera singers could break crystal glasses by singing at the right frequency; it’s only fitting that our modern “opera” singers, whose voices are now stored in MP3, OGG or FLAC (if you’re into gold-plated audio cables), can blow up digital storage through the power of RESONANCE! As you can see in Figure 4, if your exciting frequency is super close to the resonant (aka fundamental) frequency of your system and the quality factor is high, then things go BOOM.
Who cares?
Obviously, the person who went through the hassle of resurrecting this issue from the Windows XP days and filling a 2022 CVE must really care about this, or maybe they are really into performance art. Maybe bureaucratic paper filing is their vibe. Anyone else should take this as an opportunity to marvel at the awesomeness of physics. If you don’t care about it, I’m sorry to say we aren’t on the same wavelength (∝ 1/frequency).
What can I do?
Take a deep breath. I know this bug is scary, but look at it this way: Your computer is likely to have an SSD drive, meaning it doesn’t have any rotating platters that might vibrate, so you’re good. If somehow you do have a 5400 RPM hard drive and are using Windows, you’re also good, as the fix was implemented in XP. And if you happen to be a Linux user, your audio probably doesn’t work anyway, so all is fine, right?
Instead of worrying about exploding hard drives, maybe ponder why bugs affecting hardware from the last millennia are getting CVEs released in 2022, but security tools that are used to parse malware just get a cheeky release note mentioning arbitrary code execution but don’t get a CVE.
RECENT NEWS
-
May 13, 2024
Seven Trellix Leaders Recognized on the 2024 CRN Women of the Channel List
-
May 6, 2024
Trellix Secures Digital Collaboration Across the Enterprise
-
May 6, 2024
Trellix Receives Six Awards for Industry Leadership in Threat Detection and Response
-
May 6, 2024
Trellix Database Security Safeguards Sensitive Data
-
May 6, 2024
92% of CISOs Question the Future of Their Role Amidst Growing AI Pressures
RECENT STORIES
The latest from our newsroom
Get the latest
We’re no strangers to cybersecurity. But we are a new company.
Stay up to date as we evolve.
Zero spam. Unsubscribe at any time.