Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Dismantling a Prolific Cybercriminal Empire: REvil Arrests and Reemergence
By John Fokker · September 29, 2022
We’ve recently seen reports that the REvil ransomware gang is back online after the January 2022 arrests of several its members by Russian authorities claiming to dismantle the group and the November 2021 arrests of two members by U.S. authorities. While it remains to be seen if this re-emergence of REvil includes its most aggressive members with the same technical skills or is merely a copycat group lifting off the old name and parts of the infrastructure, we have seen a steady stream of new REvil binaries in the wild. Currently our main hypothesis is that one or several individuals have gained control over the old REvil Happy Blog and some binary source code. It is important to note that REvil was already a re-branding of GandCrab to gain influence and attention, therefore it is remarkable that the name REvil, given its infamy, is being used again/still. This gives us reason to believe the original key members of REvil group are most likely not involved.
However, reemergence or not, it has our interest.
The Trellix Advanced Research Center’s threat intelligence group has long-studied REvil, its predecessor GandCrab and other actors like them. In this blog we will often reference research we have done in the past on both GandCrab and REvil. For those interested in previous research we have performed check the following blogs:
REvil;
Episode 1: What the code tells us
Episode 2: The Allstars
Episode 3: Follow the Money
Episode 4: Cresendo
To defend against cybercriminals, we must understand how they think and how they work. To truly end operations of a cybercriminal enterprise, or a ransomware operation in this case, the individual person or group responsible for a cyberattack has to be discovered and prosecuted, but it can be notoriously difficult for law enforcement to determine who those affiliate members behind specific attacks are. Leading up to the FBI’s seizure of funds stolen by REvil and the indictments and arrests of some of the group’s members, Trellix described a novel technique to enumerate key ransomware gang members. We described this extensively in our VB2019 publication on GandCrab and a past REvil blog. In this blog, we will take you all the way from the steps REvil took to build their cybercriminal enterprise through the missteps that eventually led to their downfall.
Building a cybercriminal enterprise
Our team’s research into Conti reiterated much of what we learned from our study of REvil. Cybercriminal groups are growing in their sophistication and operations, building everything from HR, to payroll, to culture and employee recognition programs, to call centers. They are fully functioning organizations, with marketing and user support. And as they scale and build trust in and dependencies on others, they often open doors for researchers and law enforcement to poke holes in their operations and techniques which can provide new ways to uncover who exactly their affiliate members are.

When we think of a cybercrime “empire,” here are the key ingredients we expect to observe in the wild:
- Stable Product: For a group to be successful, it must have an easy to use and stable malware, and in the case of ransomware, an even more stable decryptor.
- Technology & Marketing to Scale: Many ransomware groups and other cybercriminal gangs promote their activities, mission, and job postings on carefully curated dark web sites used to instill fear in victims/potential victims. The way an organization brands itself is also critical to attracting and retaining affiliate members. To scale a Ransomware-as-a-Service (RaaS) group we often observe groups deploying a centralized panel to communicate with victims and request binaries and decryptors, as opposed to negotiating via email with hundreds of victims at any given moment.
- The Right People: Hiring the most talented affiliates is important, but as with many enterprises, many groups will still require members to complete trial periods to prove they are a fit.
- Strategic Partnerships: To scale even more, cybercriminal groups leverage partnerships to execute areas of their business – everywhere from malware obfuscation services to call centers to Bitcoin laundering services. This allows the group to focus on their own specialty.
- Pay Your Debts: Loyalty is perhaps the most important factor in keeping cybercriminal groups operational. Malware authors have made it easy for management to know what they’re owed by creating a tracking mechanism to determine commissions across the team responsible for an attack.
Signs of an organization on the edge of falling are often seen when they forget to stay humble and loyalty goes out the window or they make a sloppy mistake. The growth of the infrastructure and operations and human capital means growth of opportunities to mess up and increased likelihood for investigators like us to find novel ways to study them.
REvil in action
REvil first appeared in the wild in as Sodinokibi at the end of April 2019. Emerging from the GandCrab group, Sodinokibi aka REvil, the group quickly established operations, building a high-volume RaaS empire responsible for the theft of millions of dollars across countries and industries, and some of the most significant ransomware attacks in recent history. RaaS groups operate with a core group of people maintaining the code and another group, known as affiliates, spreading the ransomware. Additional support functions and partners are key to operations, and it is common for RaaS groups earn a commission on ransoms collected from victims. However, there were also groups like the Conti group that instead of paying a percentage had their affiliates on payroll.
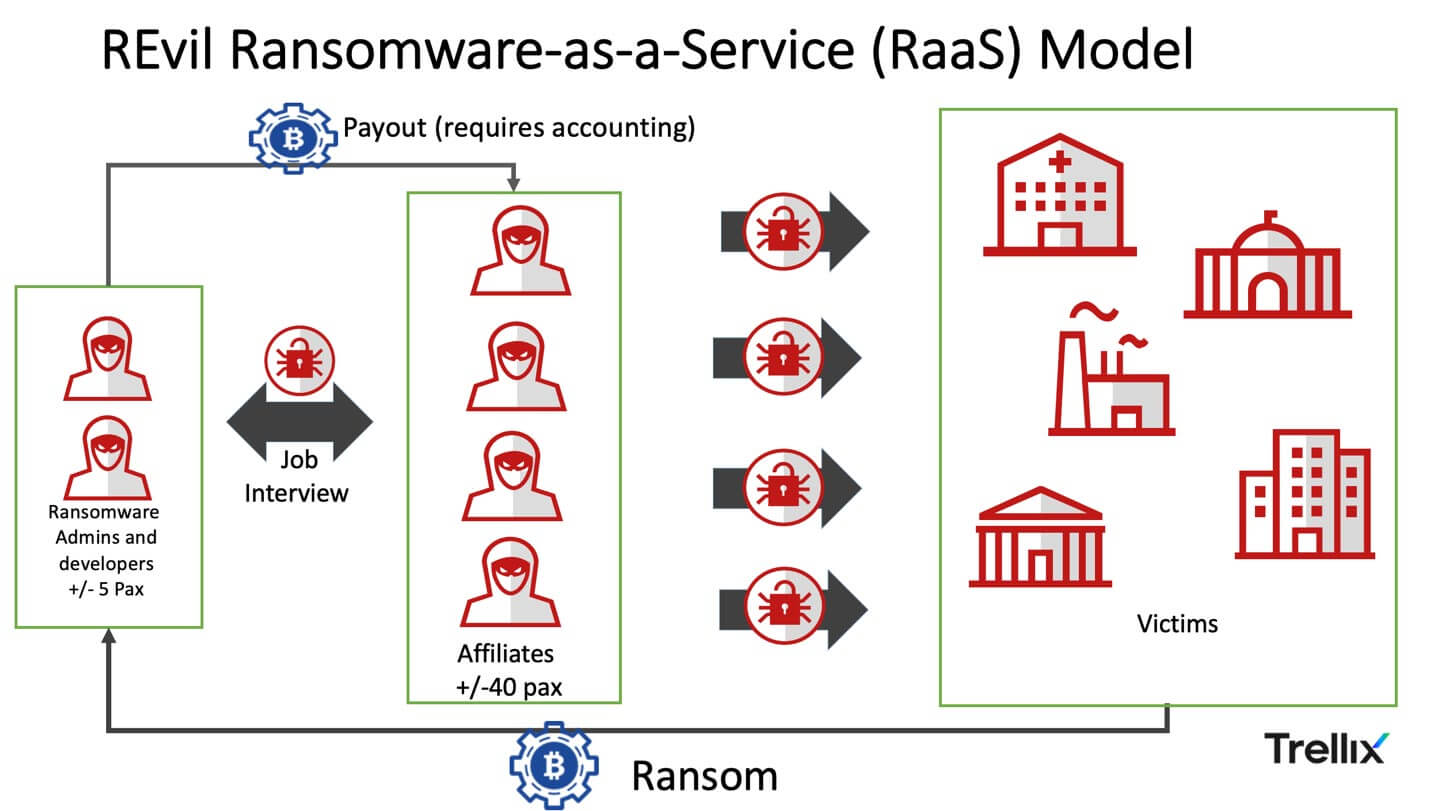
REvil was behind some of the biggest ransomware attacks in recent history, including attacks on Kaseya VSA which impacted a number of managed service providers and their customers, even taking 500+ grocery stores offline, and JBS SA, halting production for the world’s largest meat processing company.
The attack on Kaseya was in many ways a catalyst for an overt global law enforcement action against REvil and its affiliates. The organization’s impact had reached the food supply and its ransom demands sharply increased. In fact, the average ransomware request grew from $5,000 in 2018 to around $200,000 in 2020, a 3900% increase in just two years. The year 2021 illustrated the increasing sprawl of organizations that were impacted by ransomware, negatively impacting millions of people’s lives.
A global collaboration of law enforcement, national government agencies and private sector partners worked together to examine REvil, locate key infrastructure, communications, financial streams and determine individuals behind attacks and bring them to justice.
Determining affiliates: attribution is hard
Because of the underground nature of RaaS and other cybercriminal groups, determining affiliates responsible for executing specific ransomware attacks can be challenging. But in the case of REvil, we found something interesting.
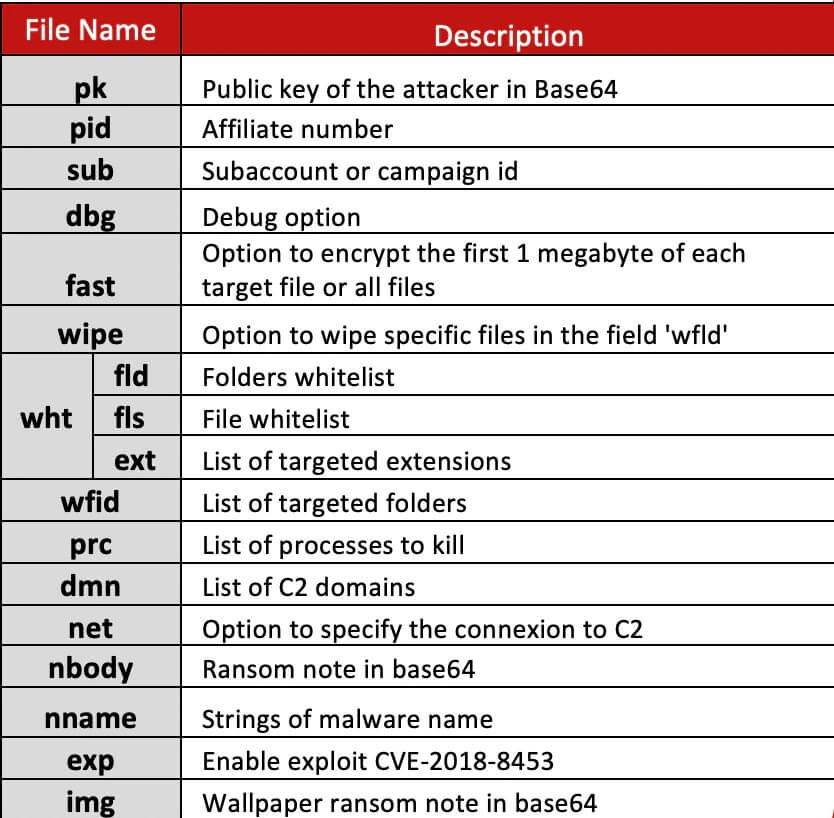
Infection administration
When we outlined what is required for a well-functioning cybercriminal group, we noted the importance of paying your people to maintain loyalty. This requires these groups to have a strong method to track their ransomware usage to ensure each affiliate member, administrator and partner is paid their commission in a timely way. As shown in the figure above REvil solved its accounting headache by including a JSON config file with each binary they built. This config file would contain several parameters and flags that were set for the ransomware, the two parameters we will be focusing on here is the pid and sub. The pid is also known as the Partner ID or affiliate ID, and the sub is known as the campaign ID and corresponds to a specific attack. There is a Parent-Child relationship between the two, an affiliate ID could be linked to multiple campaigns however each campaign we observed only had one parent. The only time we saw a single campaign ID with multiple parent affiliate IDs was when a real REvil sample was modified by a legitimate company to test efficacy in their product.
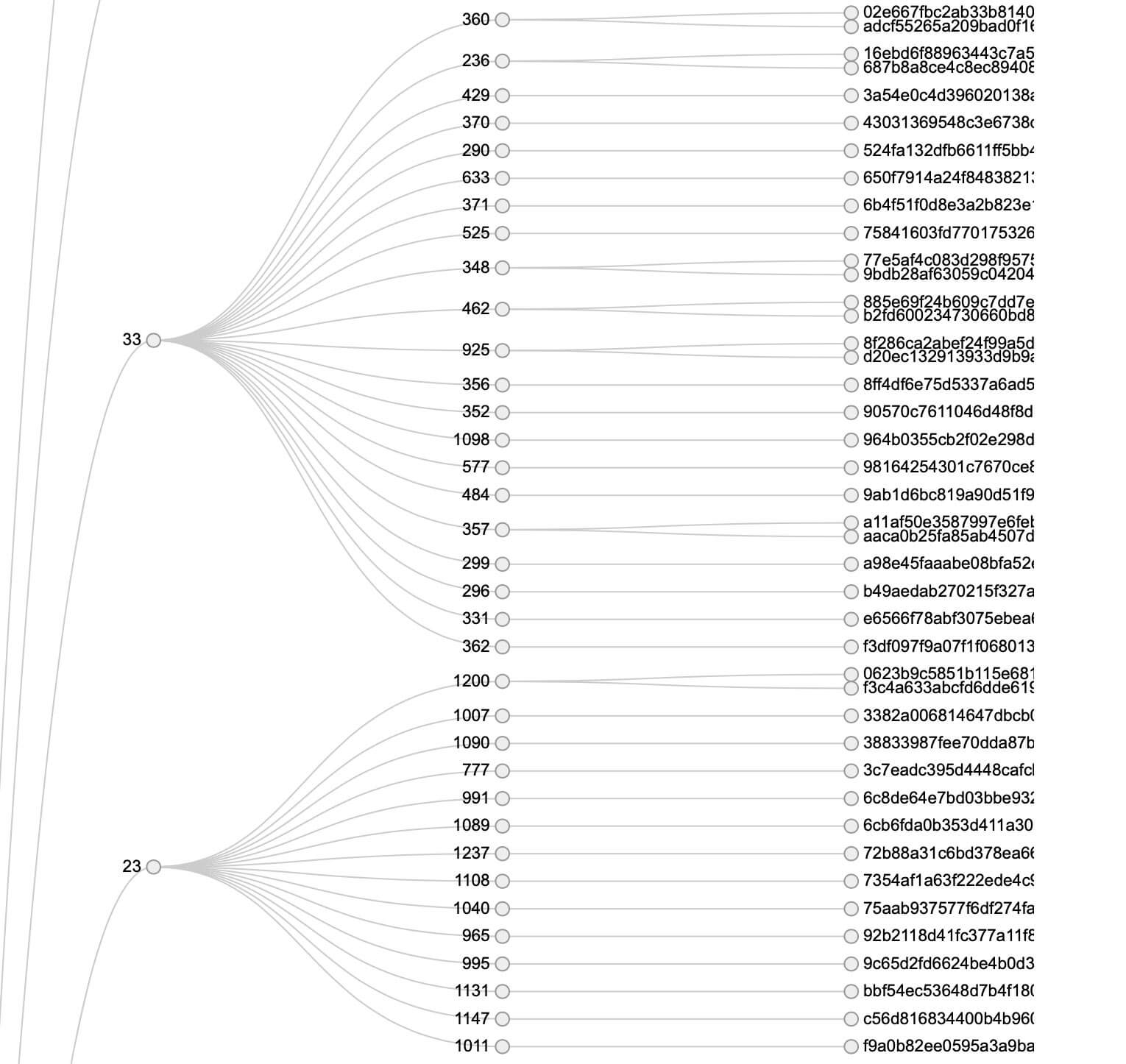
As we studied REvil and start collecting multiple samples, we noticed the recurrence of the affiliate numbers when tracking infections. REvil operated with something like an employee number. Please note that the correct labeling and function of each parameter in the configuration file wasn’t clearly defined at the start. We collected thousands of Revil Binaries and extracted their configurations, like the example above. Essentially, by creating an overview of their affiliate activity and determining who was the most active through linking the exact binary hash to a binary found at a victim we have an ability to determine which affiliate ID was responsible for which attack. Easy for the REvil administrators to pay out the right percentage to the affiliate but also handy forensic accounting for researchers and law enforcement. As we explained earlier, this was the era where ransom demands started to skyrocket, and if a victim had any chance of making a claim on the ransom through legal procedures, it had to be 100% clear which affiliate was responsible for which attack regardless of if the actual affiliate was arrested or not.
Therefore, we built a custom configuration extraction tool that was used internally and shared with Law Enforcement. This tool was a slight modification of a similar tool we developed for REvil’s predecessor GandCrab.

The use of ID numbers opened an important door to be able to track the individual activity of REvil’s team members. Some especially persistent affiliates made as much as $300,000 in one weekend.
Help from within….
Circling back to loyalty; it is ultimately a disgruntled internal source who reached out to Trellix which enabled us to glean more information on the organization and broadened our ability to deliver actional information to authorities.
In reaction to a blog we posted by in October of 2019, we received an email from an anonymous source by way of our Public Relations team. This anonymous source was not amused to read how a high-level threat actor was bragging about his weekend earnings, while the source was still waiting to be paid for infostealer logs the source supplied to this specific threat actor.
The source claimed to have identifying information on high-level criminals within REvil but wanted a financial reward in return. Before we proceed, it’s important to underscore that Trellix will never pay a cybercriminal for information. Using Trellix’s longstanding relationship with law enforcement, we were able find the right law enforcement partner to act on the anonymous source. However, they needed some time to prepare before we could hand over the source.
This gave us time to engage and try to get a better understanding of the relationships and innerworkings of REvil and its members. The REvil backend apparently had an option to show a guest around, and our source at the time was shown around by an affiliate and luckily for us he managed to take multiple screenshots.
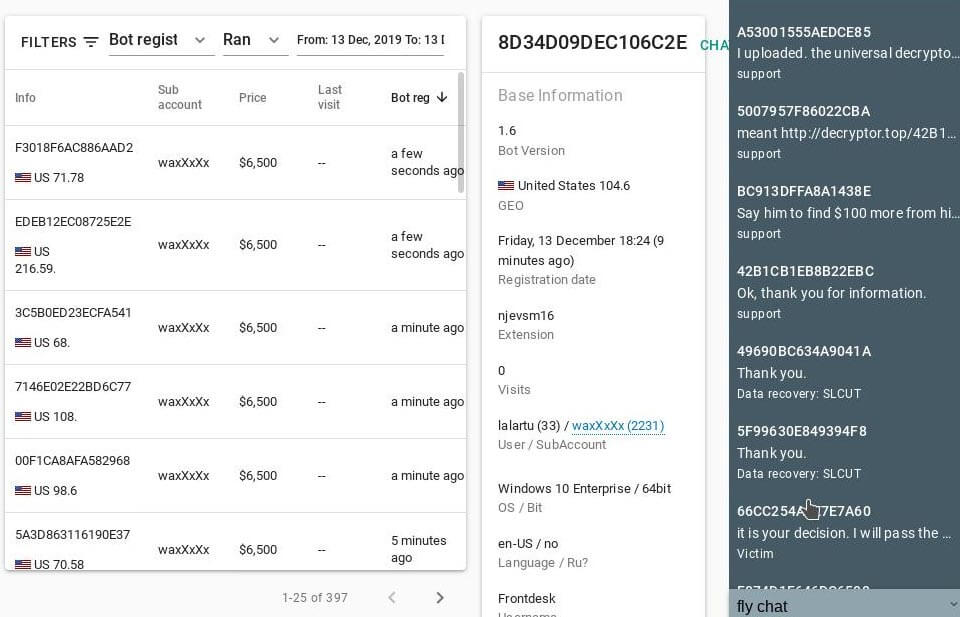
The source shared multiple screenshots of the actual REvil backend panel. The Left side of the panel showed an overview of the infected victims including country and ransom price. The middle column showed the details of a single infection that was transmitted back via the config file. The right screen shows snippets of the multiple negotiation chats that were ongoing.
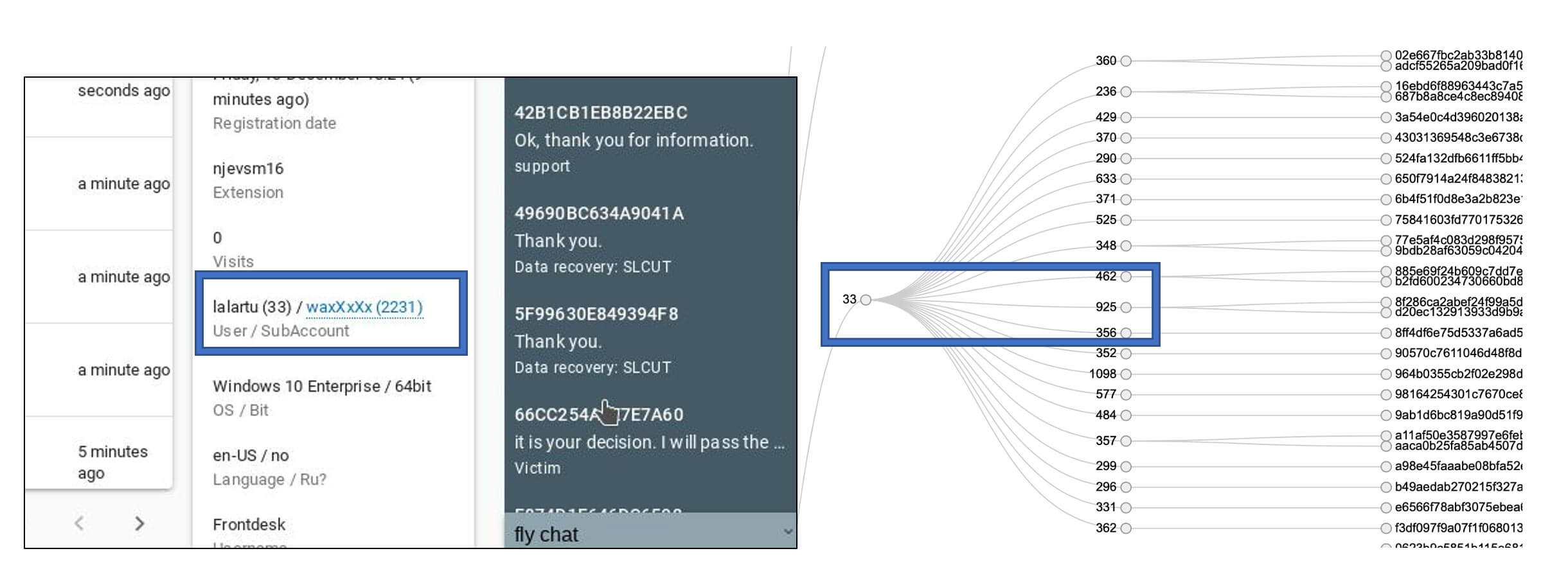
One of the most important findings from the screenshots was that it confirmed our affiliate ID hypothesis. As visible in figure 8 it clearly shows the affiliate moniker name and their affiliate ID number in brackets, the other value was the campaign ID for the specific campaign. Essentially this means this backend system had the complete affiliate roster and would make attribution a lot easier. If only we knew where it was physically located…..
Tools, tactics and techniques
The source was forthcoming, sharing TTPs, internal relationships, information on the group’s operations. The tools, tactics and techniques they used ranged from infostealer logs, RDPBrute, ADFind, Mimikatz, WinPEAS, Cobalt Strike and PowerShell scripts. This provided Trellix very useful intelligence that was quickly integrated with Trellix Insights. Please note this was even before the disgruntled Conti affiliate leaked the Conti playbook with similar TTPs online.
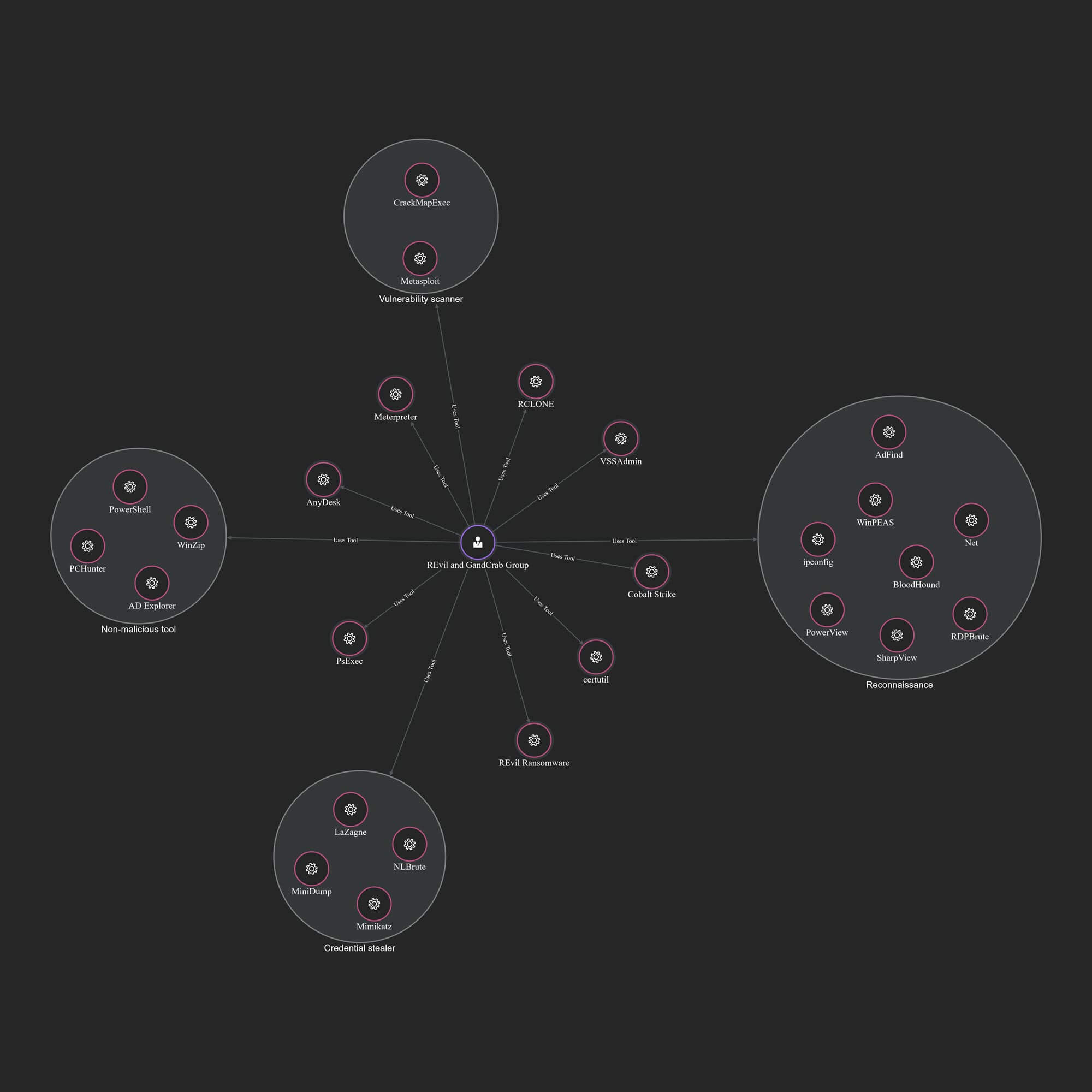
Keys to the REvil kingdom
During one of conversations with the source we asked the him how and or where affilaites would access the actual panel. The source explained that the backend panel, of which he shared screenshots, was accessed via Tor and that users had to edit their .Torrc config file to get to the panel. He then continued to share a screenshot of the login in page for the backend panel as shown in figure 10. At a first glance the panel look inconspicuous and the only thing that sort of stood out was the webpage title called Private Project.
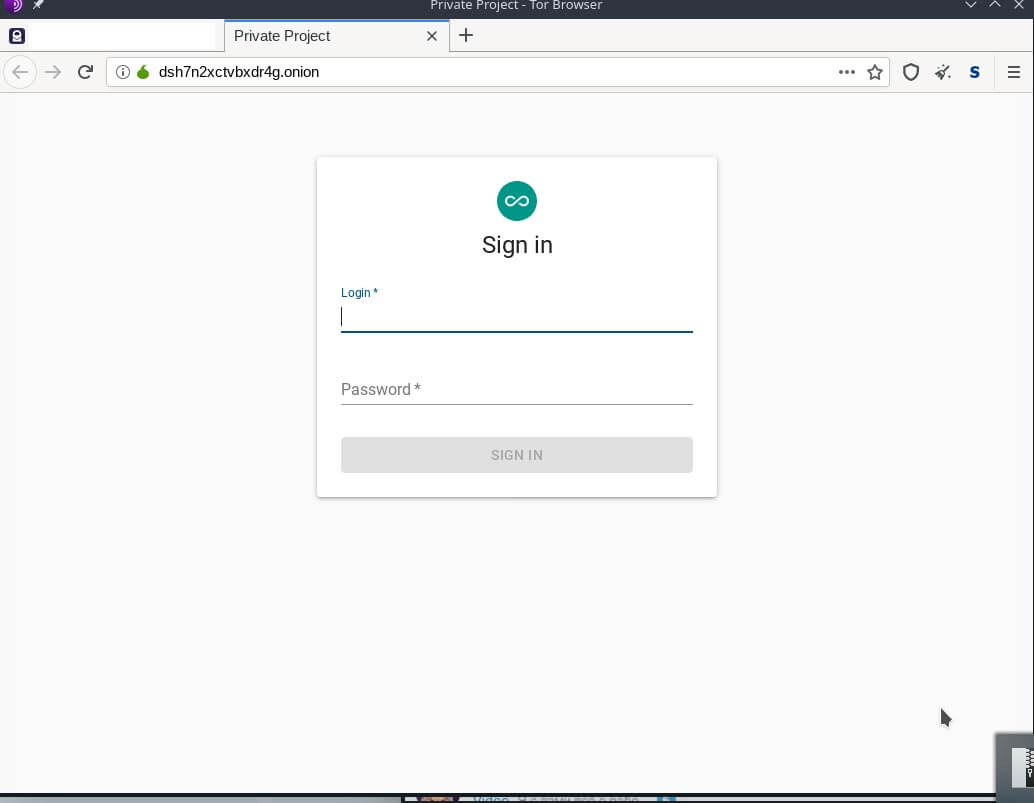
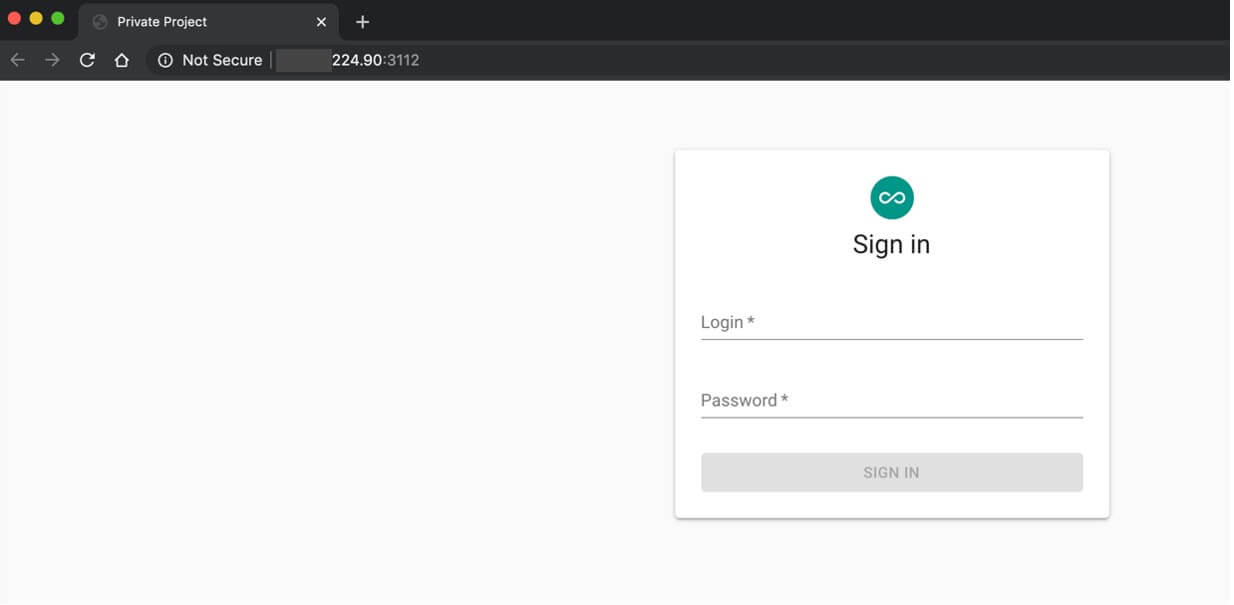
As a standard practice, our team performed a search for any webpage with the same title, using open-source search engines like Shodan and Censys, and sure enough, there were only a small number of pages on the internet with the same title—four to be exact. Three of which were actually control panels for other common malware families like Agent Tesla, however one of the fourth page was the actual REvil backend panel as shared by the source.
This meant that we had now located the physical location of the backend with a Clearnet IP address! It was no longer hidden!! We cross-referenced our findings with other sources we had and this confirmed that we were dealing with the actual backend and not a proxy. This was a definite high five moment.
This unprecedented finding was surprising, and we immediately packaged these findings together with additional analysis on individual members and the organization’s communication channels in a 55-page report for global law enforcement.
Law enforcement expressed they were ecstatic with the report and confirmed that the information provided by Trellix was of crucial importance to their investigation and other actions taken against the ransomware gang. It does show that even cyber-criminals make mistakes, we just have to be able to notice them in time.
The landscape after arrests
Following the November 2021 indictments of two group members by U.S. authorities, and the January 2022 arrests of several more members in Russia, the landscape has changed. In March of this year, a Ukrainian security researcher posted the entire internal communication of the Conti ransomware group online leading to the fragmentation of Conti and dispersing of its members.

With two large empires now fragmented and without their most resolute members, the makeup of ransomware groups is changing. Earlier this year, we suspected that REvil’s initial leaders and influential affiliates that made them notorious were a part of the Conti Gang, meaning the REvil that could be operating again is a subset of members, likely lacking the same level of influence within the gang. If REvil truly is operating again, they clearly do not have the same traction as they once did. They may have the same backend and binaries as before, but it’s highly unlikely they can match the rigor and aggression they once executed with.
Arrests of influential affiliates deter activity which is a positive sign as well. While building a case for law enforcement takes time, arrests resonate strongly in the cybercriminal underground. Given the recent changes on the world political level, we hope strongly that Law Enforcement will continue to find ways to arrest the individuals involved in spite of the challenges, as putting silver bracelets on criminals gives off the strongest message to anyone considering joining a ransomware gang.
The FBI is offering a $10 million USD reward for additional information regarding additional information on the Sodinokibi/REvil Group.
Soulful work
At Trellix we talk often about Soulful Work. We discuss the industry’s 2.72-million-person shortage and how we can do our part to get ahead of cybercriminals. This global law enforcement effort was paramount and important for Trellix to support. To return funds to organizations who paid a ransom to keep food on people’s tables is work that must be done and to see our industry collaborate – across law enforcement, government agencies and private organizations – is imperative for the greater good. There are organizations across the public and private sectors willing to go the extra mile and bring down cybercriminal groups who many assume operate without boundaries and with abandon.
This document and the information contained herein describes computer security research for educational purposes only and the convenience of Trellix customers. Trellix conducts research in accordance with its Vulnerability Reasonable Disclosure Policy. Any attempt to recreate part or all of the activities described is solely at the user’s risk, and neither Trellix nor its affiliates will bear any responsibility or liability.
This document and the information contained herein describes computer security research for educational purposes only and the convenience of Trellix customers. Trellix conducts research in accordance with its Vulnerability Reasonable Disclosure Policy. Any attempt to recreate part or all of the activities described is solely at the user’s risk, and neither Trellix nor its affiliates will bear any responsibility or liability.
RECENT NEWS
-
May 13, 2024
Seven Trellix Leaders Recognized on the 2024 CRN Women of the Channel List
-
May 6, 2024
Trellix Secures Digital Collaboration Across the Enterprise
-
May 6, 2024
Trellix Receives Six Awards for Industry Leadership in Threat Detection and Response
-
May 6, 2024
Trellix Database Security Safeguards Sensitive Data
-
May 6, 2024
92% of CISOs Question the Future of Their Role Amidst Growing AI Pressures
RECENT STORIES
The latest from our newsroom
Get the latest
We’re no strangers to cybersecurity. But we are a new company.
Stay up to date as we evolve.
Zero spam. Unsubscribe at any time.